Building an Anomaly Scoring Rule:¶
Note: Please ensure you've defined both the index definitions required by this app before building an anomaly scoring rule for the first time (which you can validate by going to Configure > Configure Indexes and Collections within the app) in addition to at least one behavioral indicator search
Following creation of at least one behavioral indicator search, you can deploy a new anomaly scoring rule by navigating to the Anomaly Scoring Rules page underneath the Deploy dropdown menu on the navigation bar and selecting Create Anomaly Scoring Rule. Anomaly scoring rules are used to attribute scores to entities based on the output of underlying Behavior Indicator Searches which they take as an input. Together anomaly scoring rules create an aggregated profile of entity behavior and a ranking across your set of entities. The Create Anomaly Scoring Rule workflow guides you through the following steps:
- Choose the anomaly defining mode the rule will use
- Select the behavioral indicator profiled
- Define the scoring criteria based on the chosen scoring method
- Size the scores attributed to events which meet the scoring criteria
- Save and schedule the scoring rule
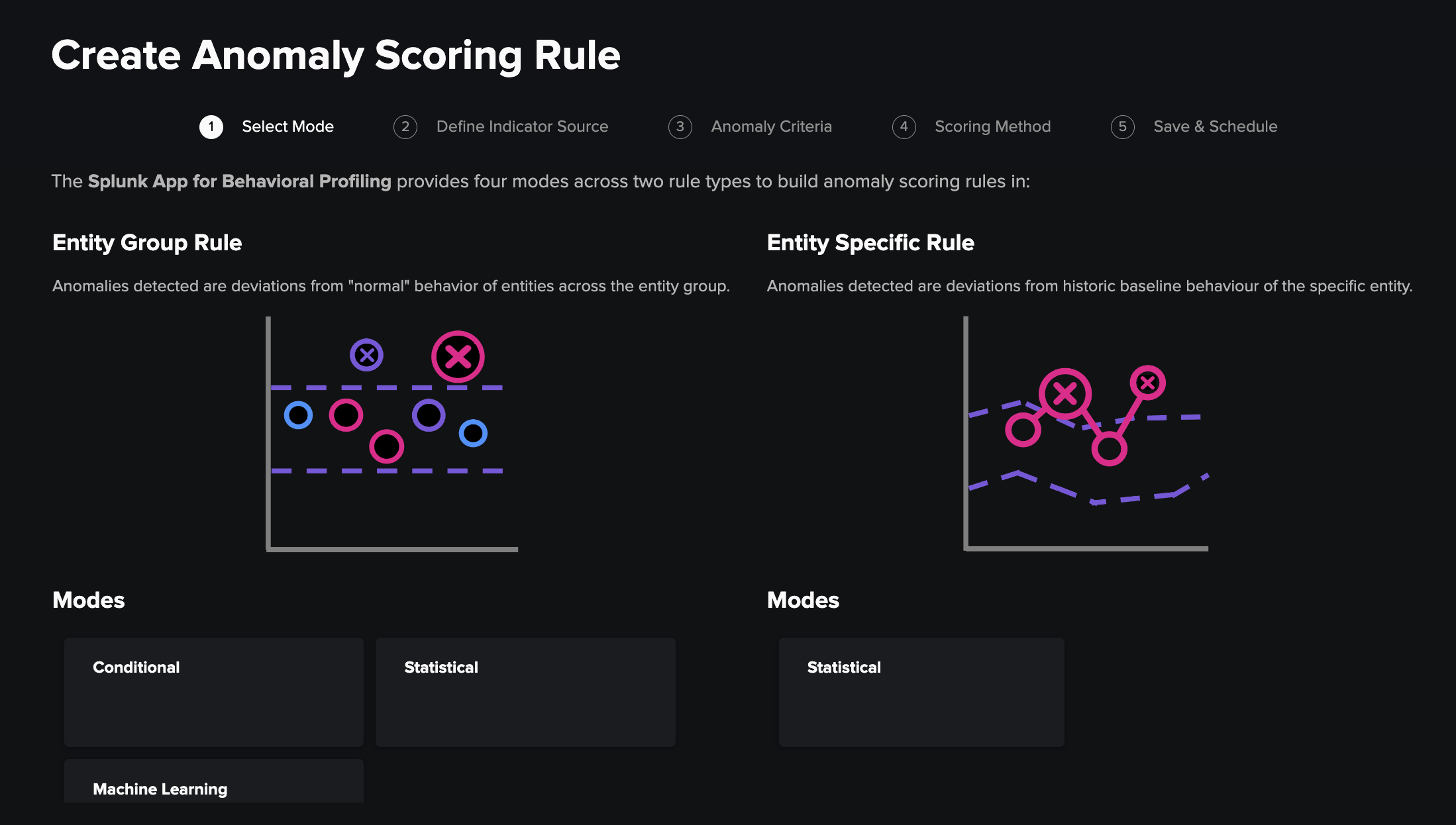
1) Select Mode¶
The first step is to choose which mode your rule will operate in. The options fall into two categories:
-
Entity Group Rules where the anomaly criteria is the same across the entity group (this is the recommended approach for groups of entities where "normal" behaviour is likely to be similar across the entity group or where there is unlikely to be enough historic data to create per entity baselines). This category comes in three variants:
- Conditional: events are filtered for scoring based on a comparison between their scoring field value and a static input.
- Statistical: anomalies are determined by appearing outside a threshold based on standard deviations away from the mean indicator value.
- Machine Learning: a distribution profile of the scoring field is defined and a threshold tolerance is specified to detect anomalous values with machine learning.
-
Entity Specific Rules where each entity will have its own statistical baseline defining normal behavior for an indicator.
You can change between these options at any time in the anomaly scoring rule creation process by returning to this screen.
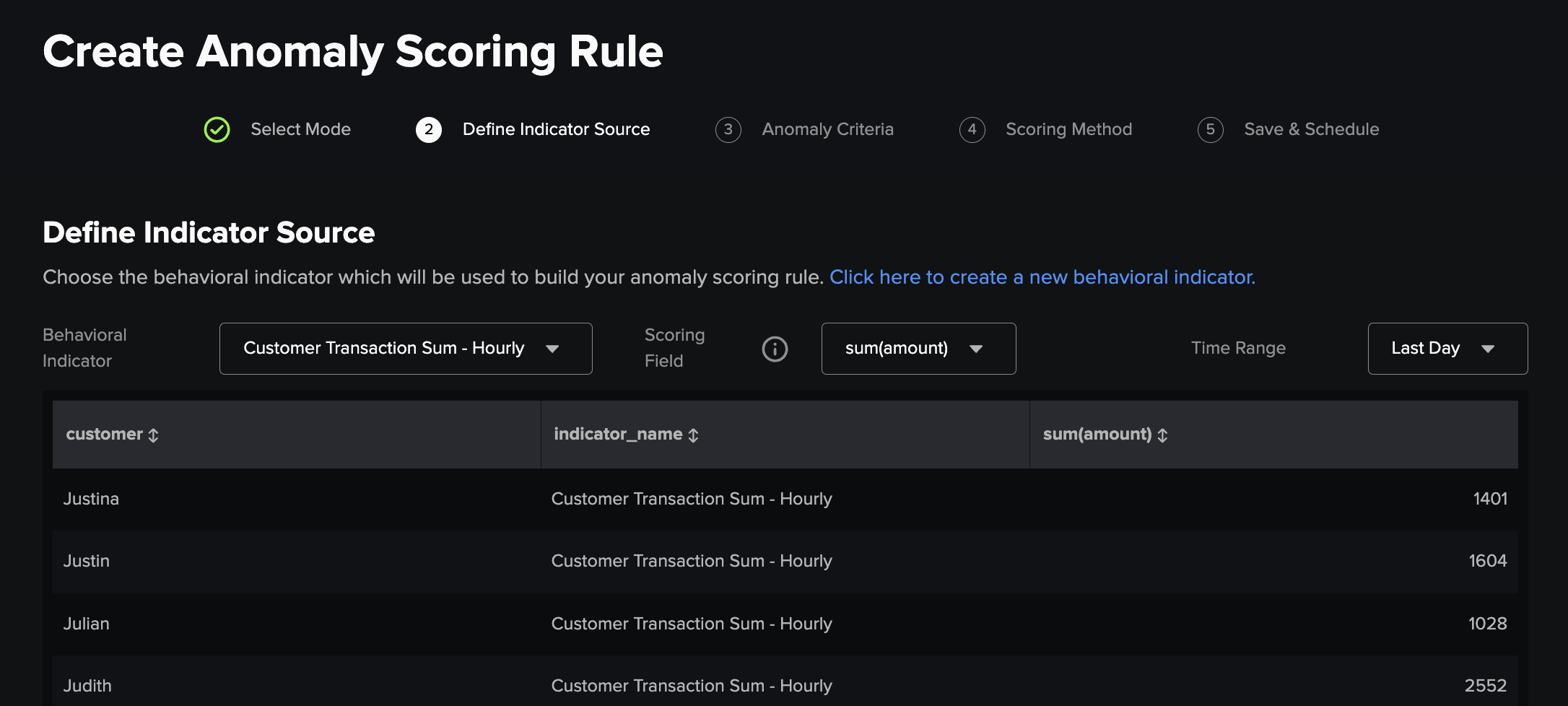
2) Define Indicator Source¶
Next, you must define the underlying settings which set the context of the scoring rule. This consists of selecting the behavioral indicator search, and scoring field within the output of that indicator search, which will be used as an input for the scoring criteria logic. Addionally, the time range set here is the window used for calculating example anomalies in the rest of the creation workflow.
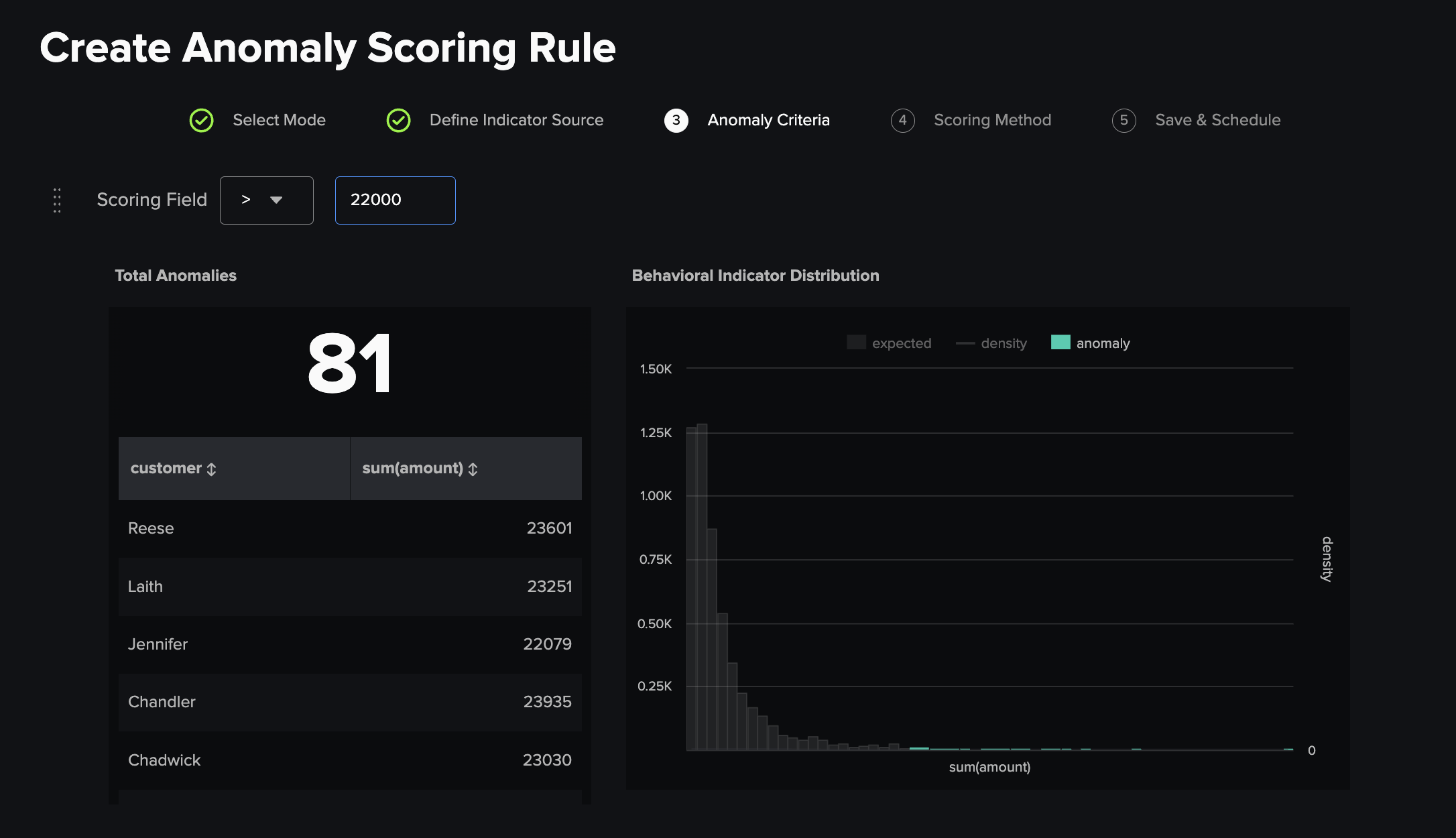
3) Anomaly Criteria¶
Entity Group Scoring¶
Conditional¶
This method enables you to create a basic conditional logic function using a static comparison, entered in the free text box, which is compared using the dropdown menu input, to the defined scoring field. Any values which fulfil the logic criteria are marked as outliers and scored.
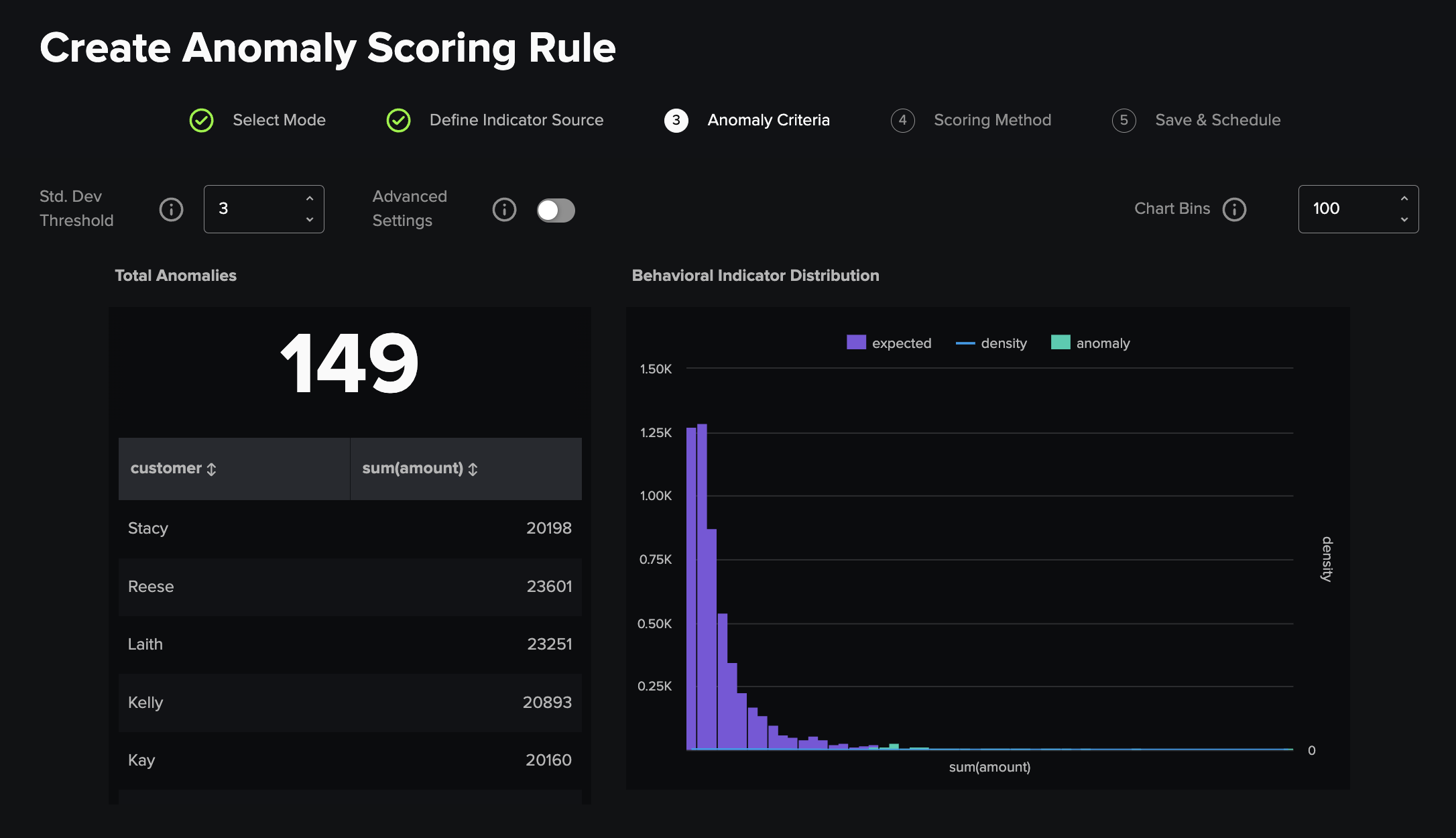
Statistical¶
This method calculates a mean value for your chosen scoring field and calculates upper and lower bounds for an outlier threshold by calculating standard deviations away from the mean. You can adjust the max upper and min lower bound values manually for specific data sets (where for example a value above or below would be impossible) via the advanced settings toggle and alter the number of standard deviations used as well as the number of bins represented on the distribution histogram chart.
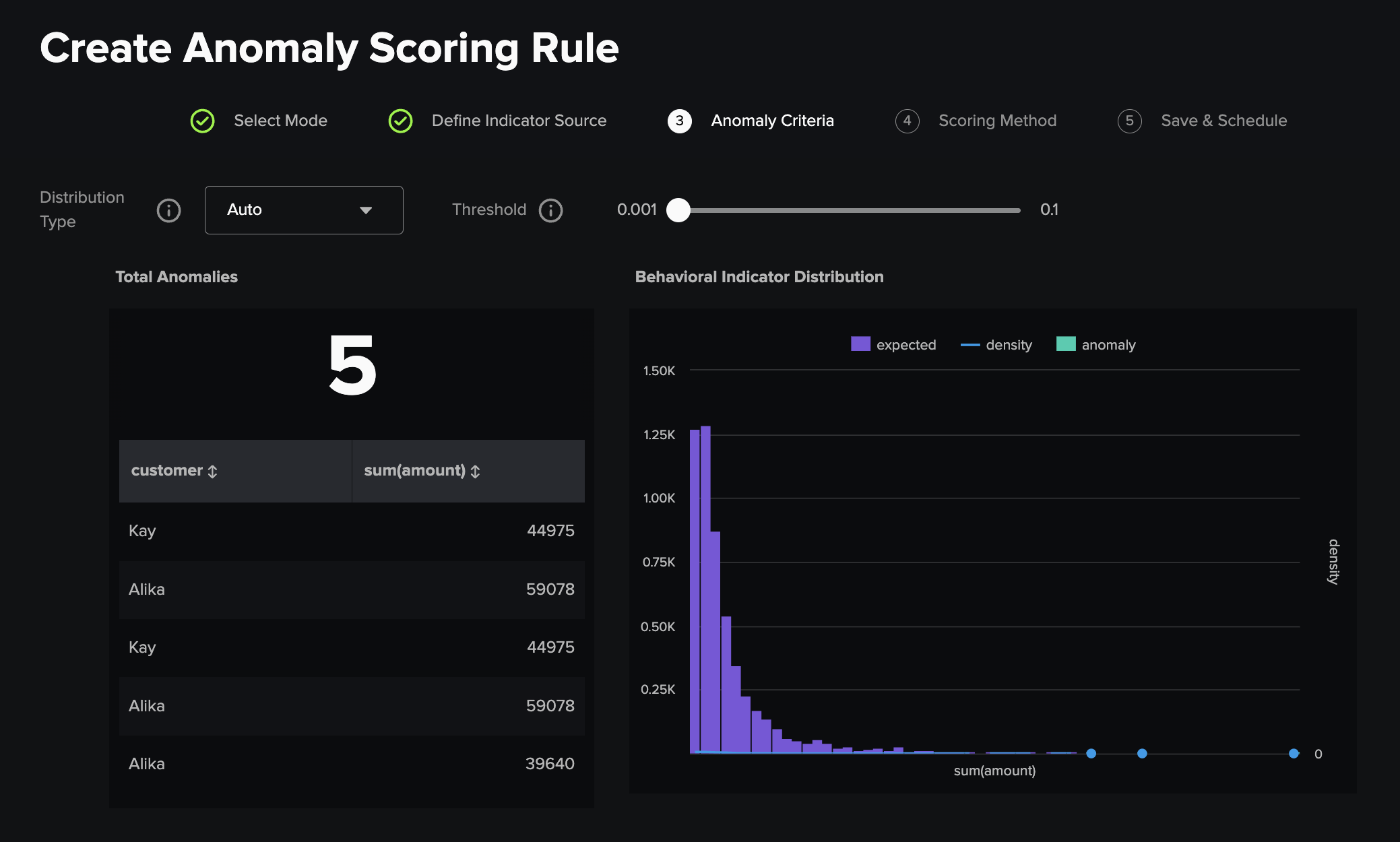
Machine Learning¶
This method utilises the machine learning toolkit density function to profile the distribution of the chosen scoring field and detect outliers based on your input Threshold from the slider, with outliers shown on the histogram and in the table to its left side. By default the Distribution Type is Auto which runs all distribution types from the dropdown menu and produces the optimal result, but you can also specify a preferred type based on the distribution of your data.
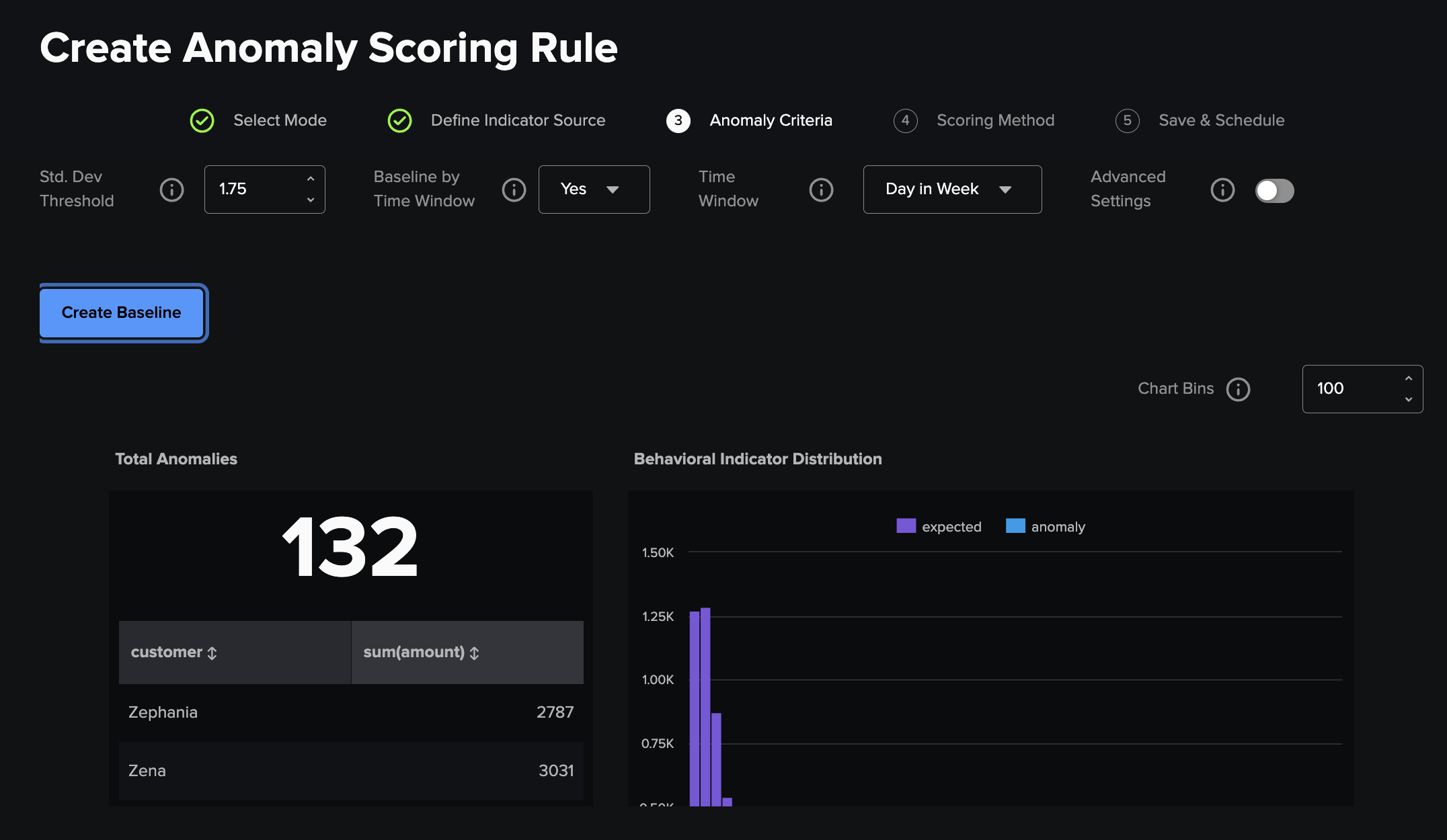
Entity Specific Scoring¶
This method enables you to define a stastical baseline for your entities, using a set standard deviation to define the non-outlier threshold for your entities and the option to have the outlier threshold for each entity split further to profile their behaviour at different times of the day, week or month. Additionally, you can adjust the max upper and min lower bound values manually for specific data sets (where for example a value above or below would be impossible) via the advanced settings toggle.
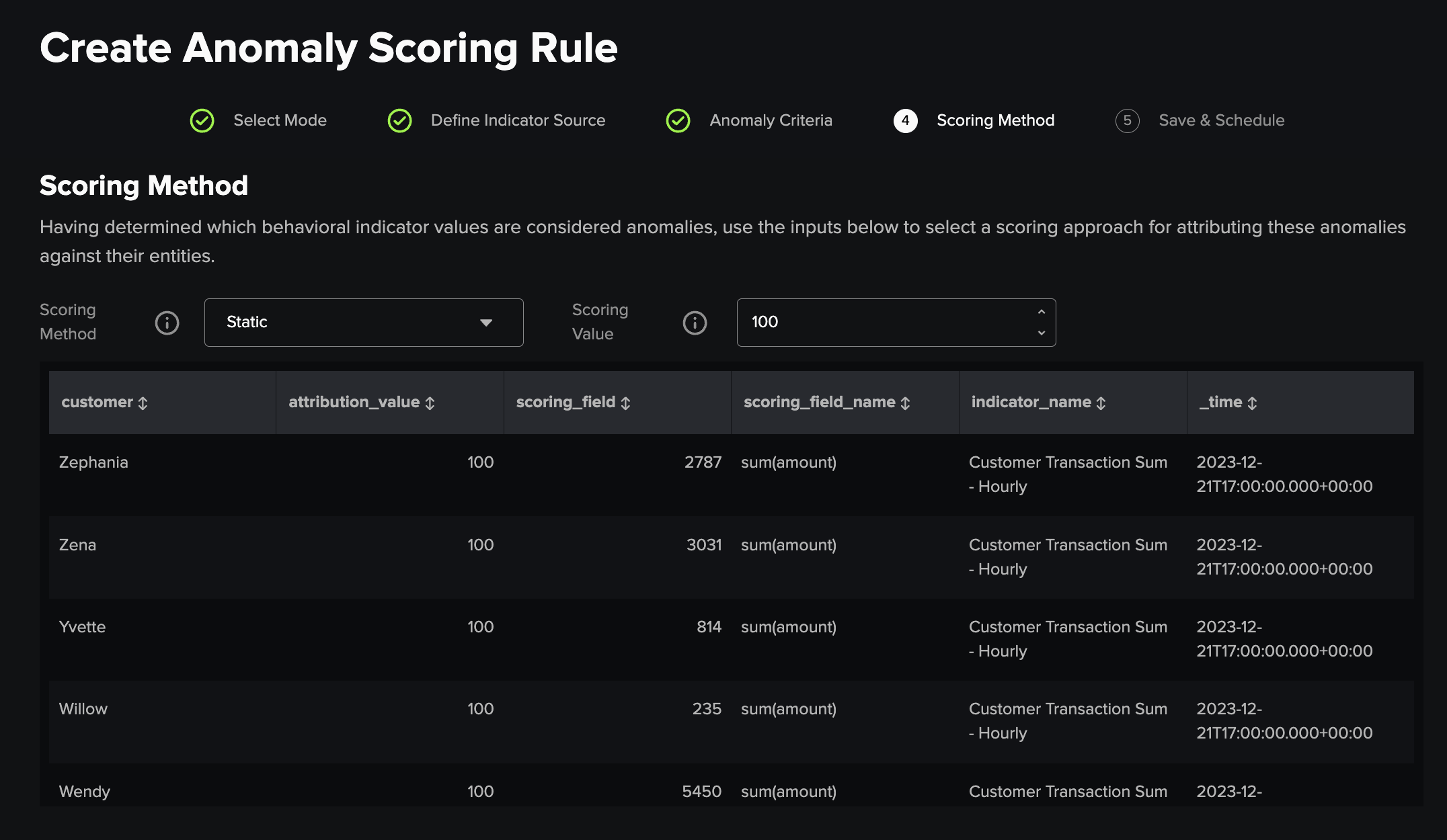
4) Scoring Method¶
Having specified the logic which decides which behavioral indicator values trigger a scoring event, the next step is to use the dropdown menus to select a methodology and input scoring value for score sizing of these events. Currently the options are either Static which attributes the value in the Scoring Value text box to the event or Proportional which attributes the multiple of this value and the scoring field value, which has been determined to be an outlier, to the event.
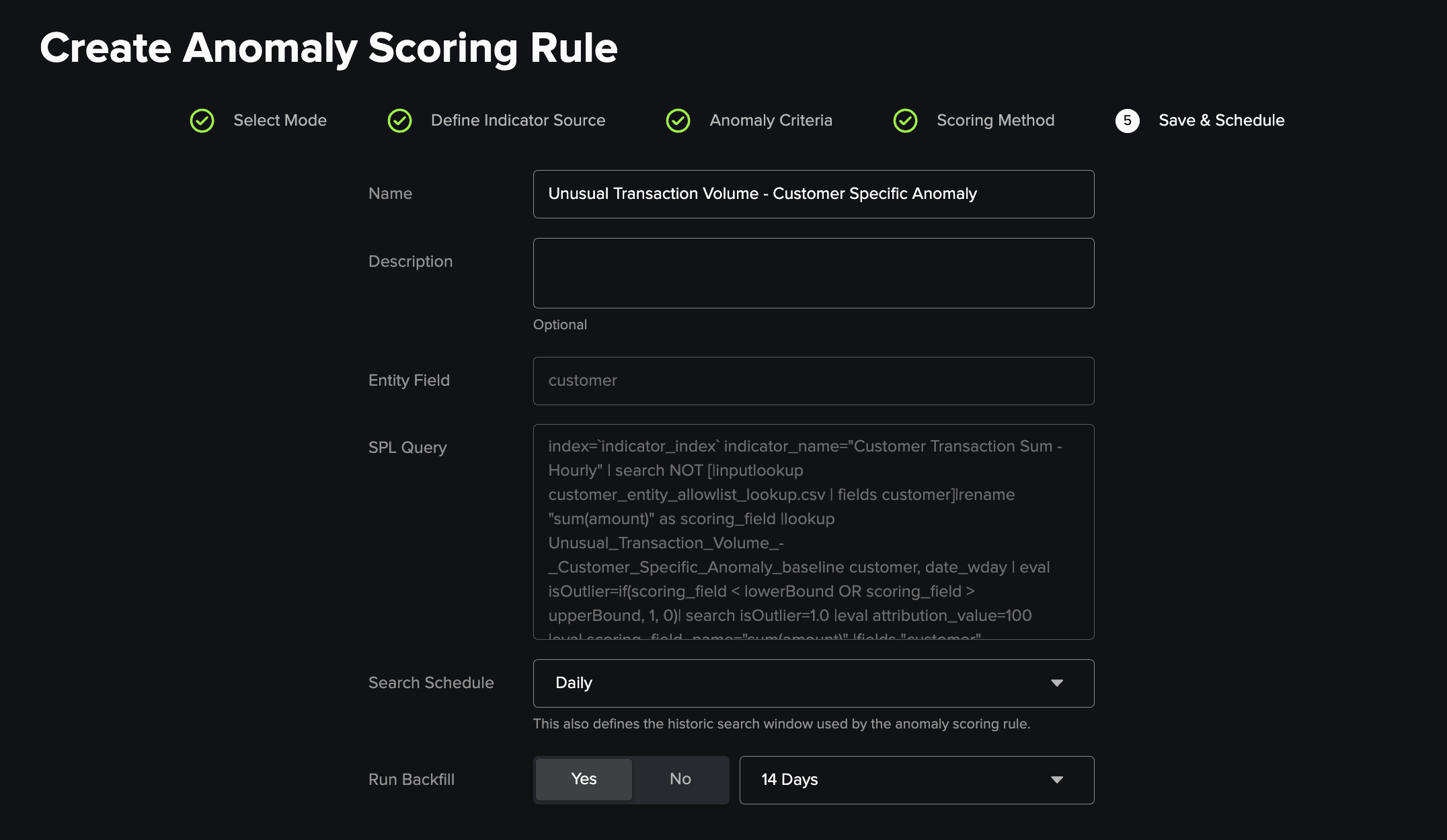
5) Save & Schedule¶
Specify a name, description and schedule for the anomaly scoring rule. These are used, when Save is clicked and Submit selected in the pop up modal, to generate and schedule a saved search which runs on the provided schedule and outputs to the defined scoring_index. If backfill is ticked, the search will additionally run immediately over the selected time window so it can populate views and be used to build a new anomaly scoring rule.
If deploying an anomaly scoring rule leveraging the Entity Specific method, you will also have to enter the refresh frequency and method, chosing between KV Store and Lookup File, for the baseline object here. KV Store is reccomended here for all instances in which your Splunk user permissions support creation of collections.conf and transforms.conf stanzas.
Additionally, logging is provided on the build status of the search, its associated KV metadata and backfill.