Overview and Purpose of NERC CIP Content¶
The Splunk for OT Security CIP components are meant to help automate CIP investigations and reports that are mandated by the NERC CIP standard. This focus is reflected in how the Scorecards and Reports are organized and how they are populated. Whenever possible, they leverage Splunk's Common Information Model (CIM) and rely on Enterprise Security's Asset framework to make implementation easier and faster for organizations.
The Administrative Guide provides key information on tagging and identification of assets that fall under NERC CIP classification.
Scorecards and Reports¶
The NERC CIP components of Splunk for OT Security are broken into two main categories:
Scorecards and Reports. Navigation in the app differentiated between the two as shown here!
All Scorecards and Reports are grouped together under CIP Numbers (e.g. CIP 002, 004, etc) to help organizations quickly navigate between the various requirements; however, there are differences between the two that are important to understand when using them for reporting purposes.
Scorecards are a collection of CIP Requirements (R2, R4, etc) for each area. They are not prefiltered for reporting purposes to auditors, but allow organizations to understand their overall posture and state and maximize flexibility when needing to investigate potential issues.
Reports are more granular and designed as a mechansm for an organization to review and then hand over the results to an auditor. In addition, reports are pre-filtered based on the NERC CIP requirements and are designed to be used as input for an audit (although depending on an auditor's request may need additional filtering). Reports do allow organizations to do some filtering to answer specific queries from auditors, for example, requests for records regarding a specific asset or user. This guide does not cover reports in depth as many are derived from similar panels on the scorecards. It is recommended that any evidence from Splunk given to an auditor first be reviewed internally.
The following section breaks down the Scorecards and Reports by their major classifications:
NERC CIP 002¶
Critical Cyber Assets¶
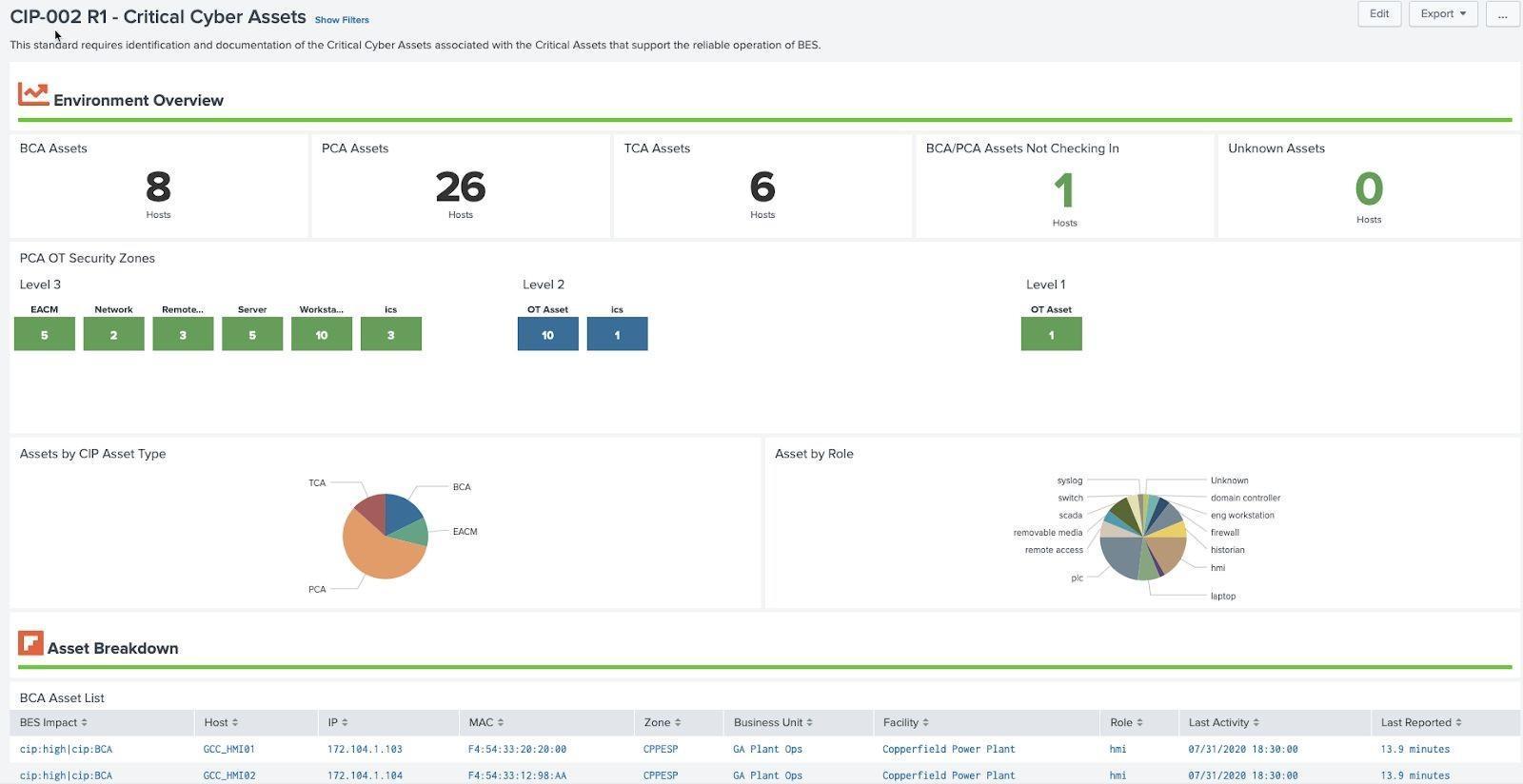
NERC CIP requires BES Cyber Systems to be classified and broken down by specific classifications and security zones. The classifications require an asset to be assigned a CIP criticality as well as CIP asset type. CIP explicitly defines criticality as Low, Medium, or High and has numerous asset types (BCA, PCA, EAP are all examples). In addition, typically at a site level an asset will be assigned to a CIP asset zone, although Splunk does not explicitly make that mandatory. The Critical Cyber Asset Scorecard provides a customer to method to understand how assets are classified in their environment. As a result, assets should be tagged with these fields as explained in the Administrative Guide. If these assets are tagged appropriately they will show up CIP 002 Scorecards and Reports automatically.
Critical Cyber Assets Example (CIP 002 R1):
NERC CIP 004¶
Security Awareness Training¶
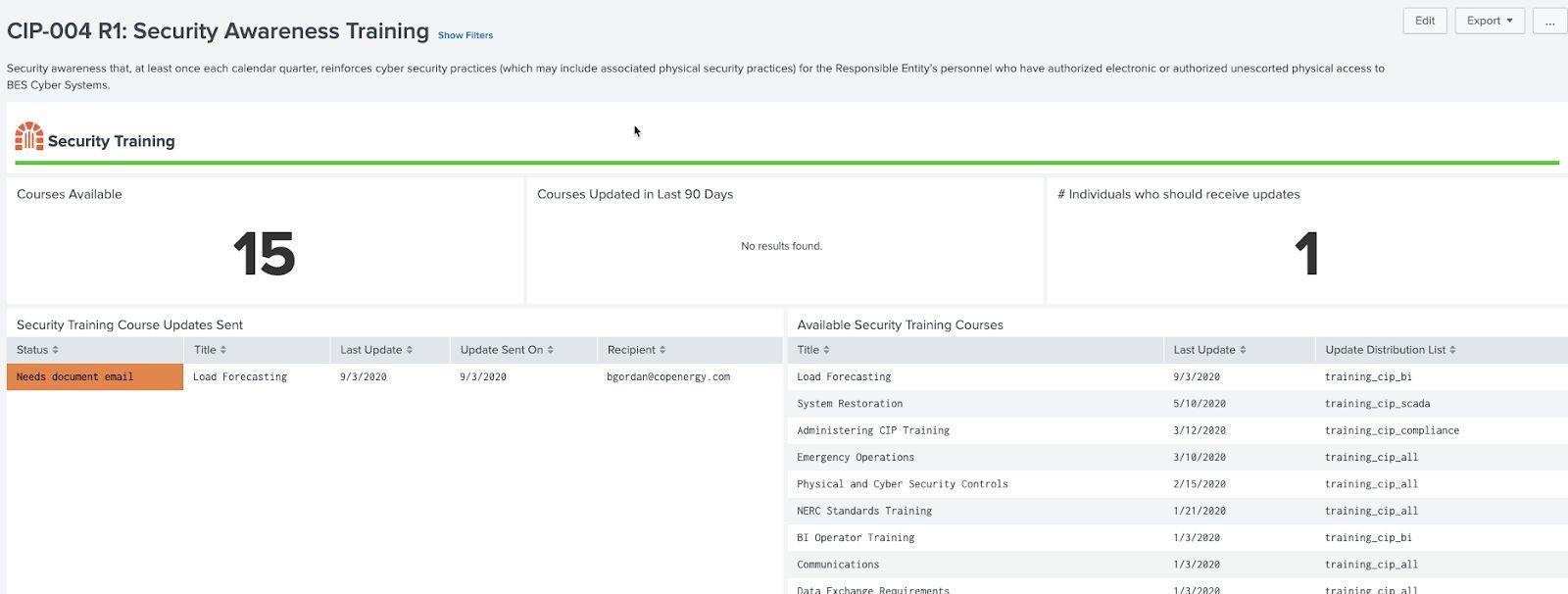
NERC CIP requires that users and operators in regulated environments complete specific training as part of the certification process. For users who require certification, they must be classified into groups which determine which training is required. In addition, updates to course materials should be communicated to individuals who have previously taken this training (normally via email). The email data model is used to identify whether notifications have been received.
Security Awareness Training Example (CIP 004 R1):
Cyber Security Training¶
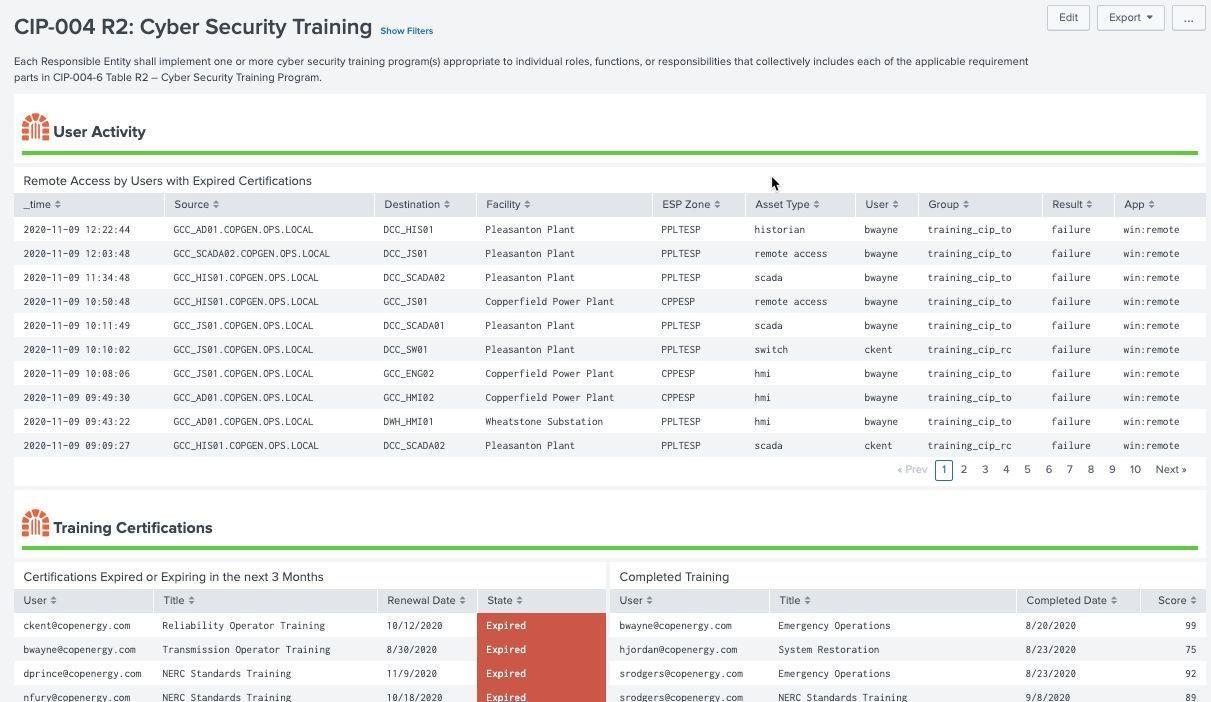
Individuals accessing NERC CIP environments must be trained and certified before accessing assets within NERC CIP environments, remotely, onsite, or physically. NERC CIP requires that training requirements be tracked and monitored for expired certifications and then correlated with access records. This dashboard makes use of the authentication data model to track to determine remote or local access to systems by individuals required to be NERC CIP certified.
Cyber Security Training Example (CIP 004 R2):
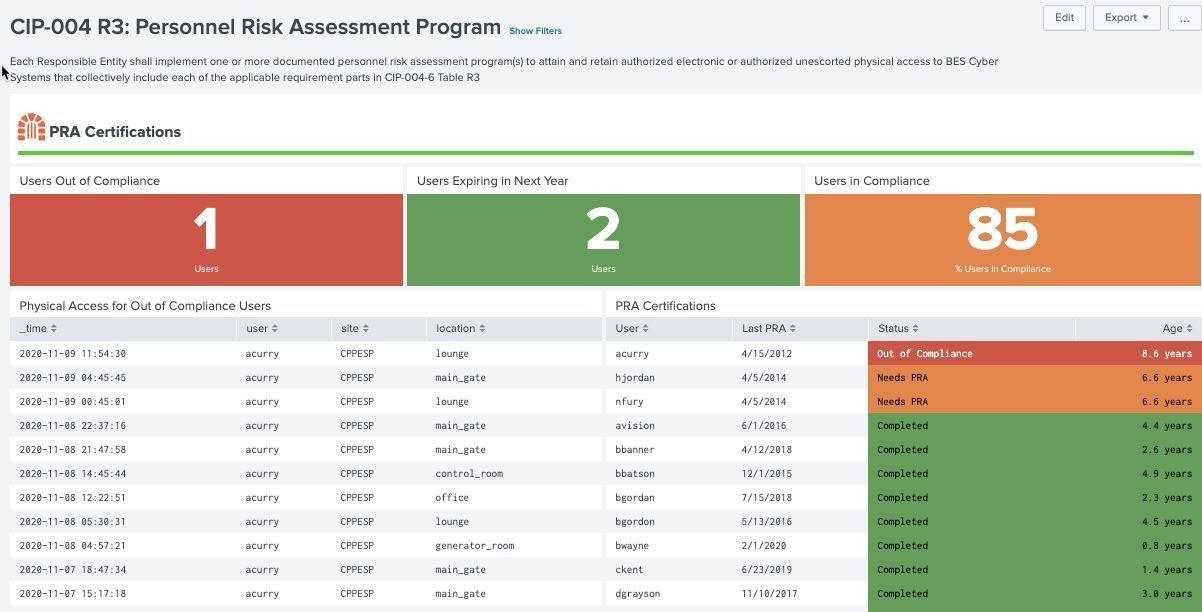
Personnel Risk Assessment (PRA) Program¶
Individuals accessing NERC CIP environments must periodically have personnel risk assessments (PRA) performed not to exceed every 7 years. This certification may be performed by outside entities, but should be tracked and recorded by operators of NERC CIP assets. In addition, access to NERC CIP environments should be monitored for individuals out of compliance.
Cyber Security Training Example (CIP 004 R3):
NERC CIP 005¶
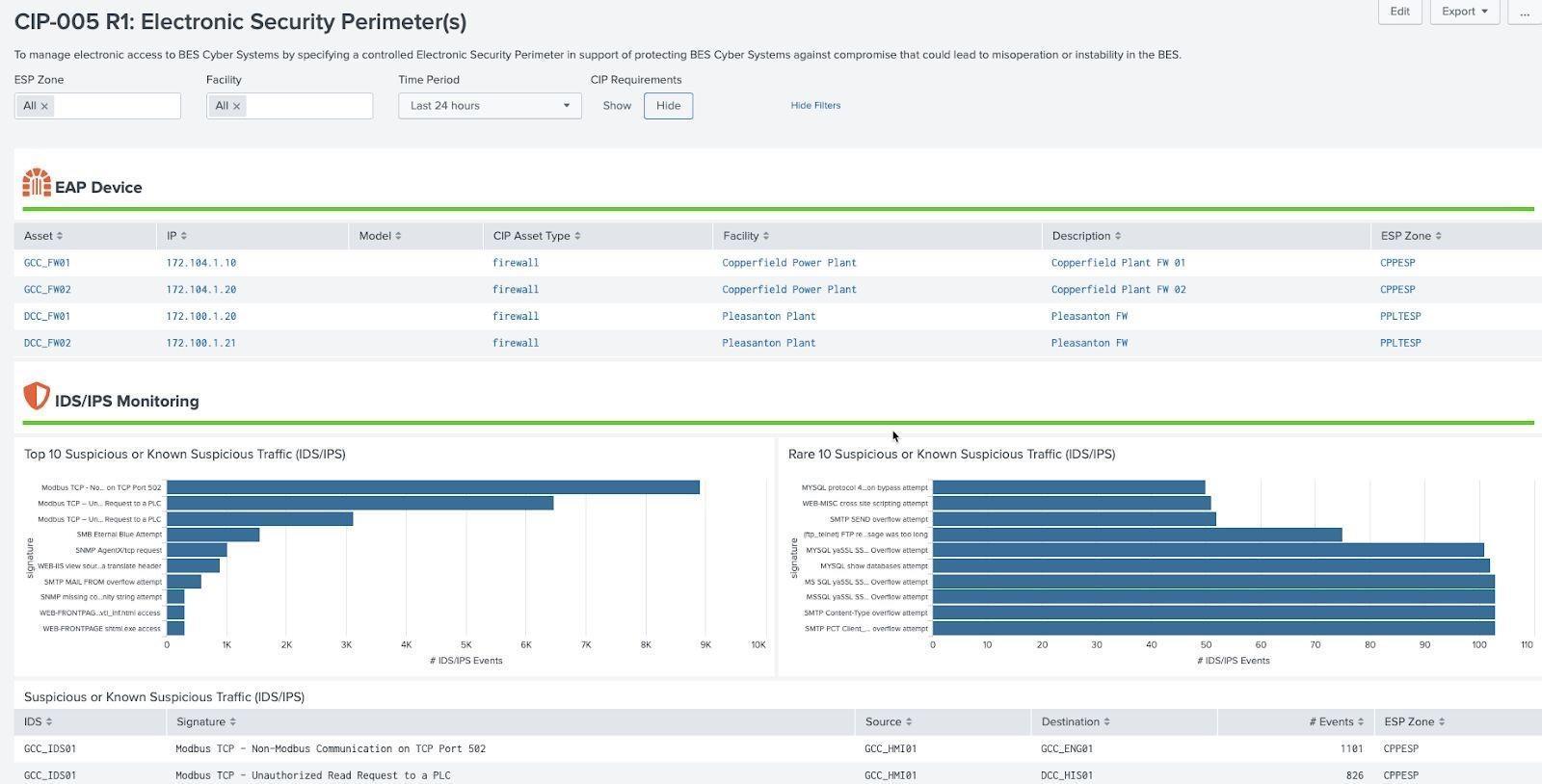
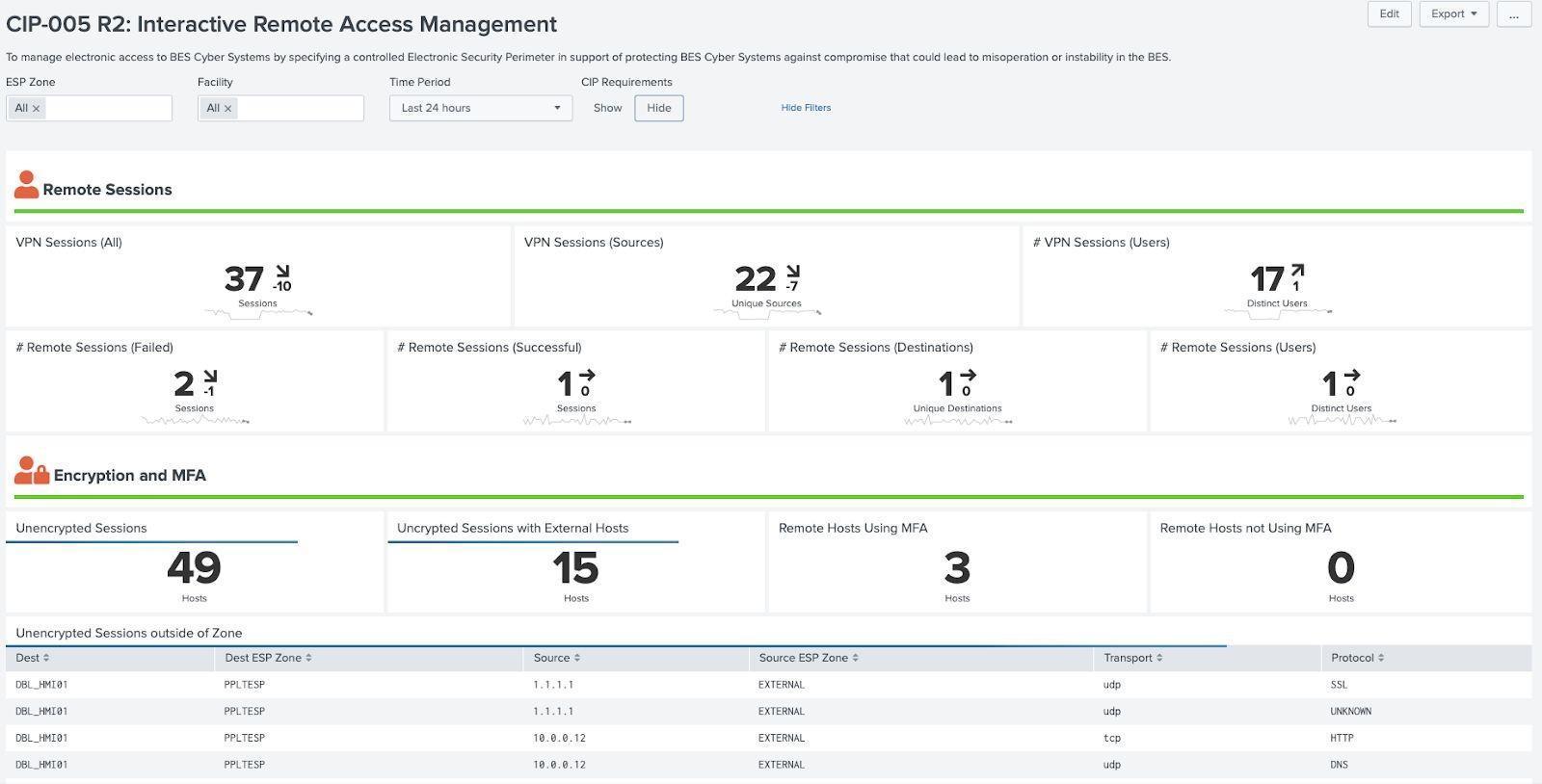
Electronic Security Perimeter and Remote Access¶
NERC CIP 005 is focused on protecting the perimeter of the NERC CIP environment by monitoring the Electronic Security Perimeter (ESP) and Remote Access into the environment. For assets which are part of the ESP (normally firewalls and data diodes), the devices must be explicitly tagged with the classification of cip:EAP in the asset framework.csv. For devices that are on the perimeter and are often responsible for monitoring ingress and egress traffic (e.g. IDS, IPS) they should be tagged with the classification of cip:EACM in the asset framework. Most ESP devices are also EACMS devices and should be tagged with both classifications (pipe delimited). Additional data sources from equipment such as networking equipment and multi-factor authentication systems help to determine if remote communications are properly secured. The macro get_2fa_indexes can be used to point to specific indexes, sources, and sourcetypes to capture multi-factor addition logs and improve search performance.
Electronic Security Perimeter Example (CIP 005 R1):
Interactive Remote Access Management Example (CIP 005 R2):
NERC CIP 007¶
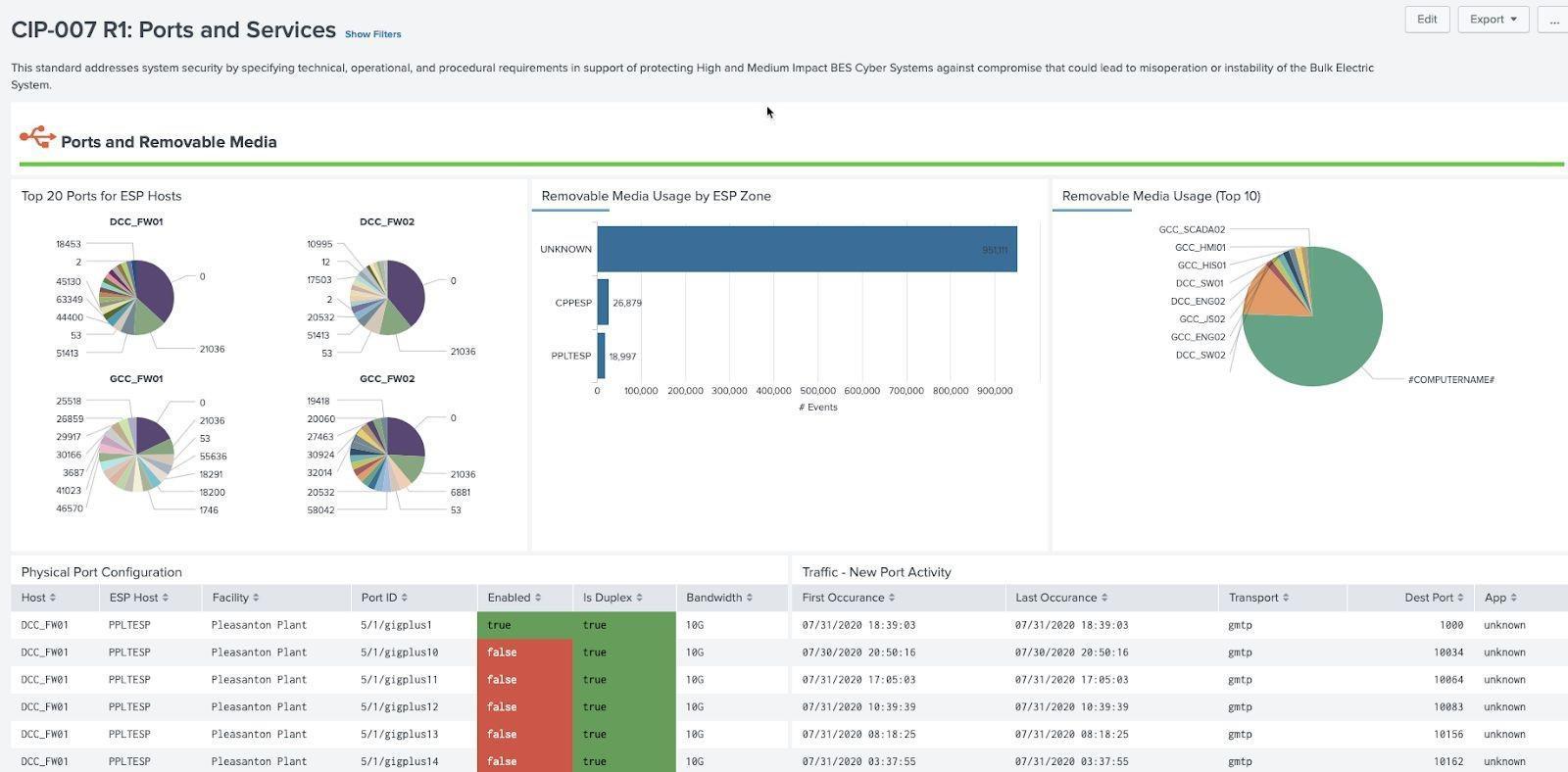
Ports and Services¶
Ports and services being used and present on machines is mandated by NERC CIP and involves a wide plethora of data sources relevant to these requirements. Firewall, routers, switches can provide information on ports being used, as well as logs from machines themselves or data can be collected via Splunk Stream. In addition, events from endpoint protection logs that monitor USB usage, or directly from Windows Events (current OS) as well as windows registry (older OS's) play a role in determining when remote media is being used. Since the source of remote media usage can vary, the macro get_removable_media_indexes can be used to point to specific indexes, sources, and sourcetypes that contain this information.
Ports and Services Example (CIP 007 R1):
Security Events, Malware Alerts, and Monitoring¶
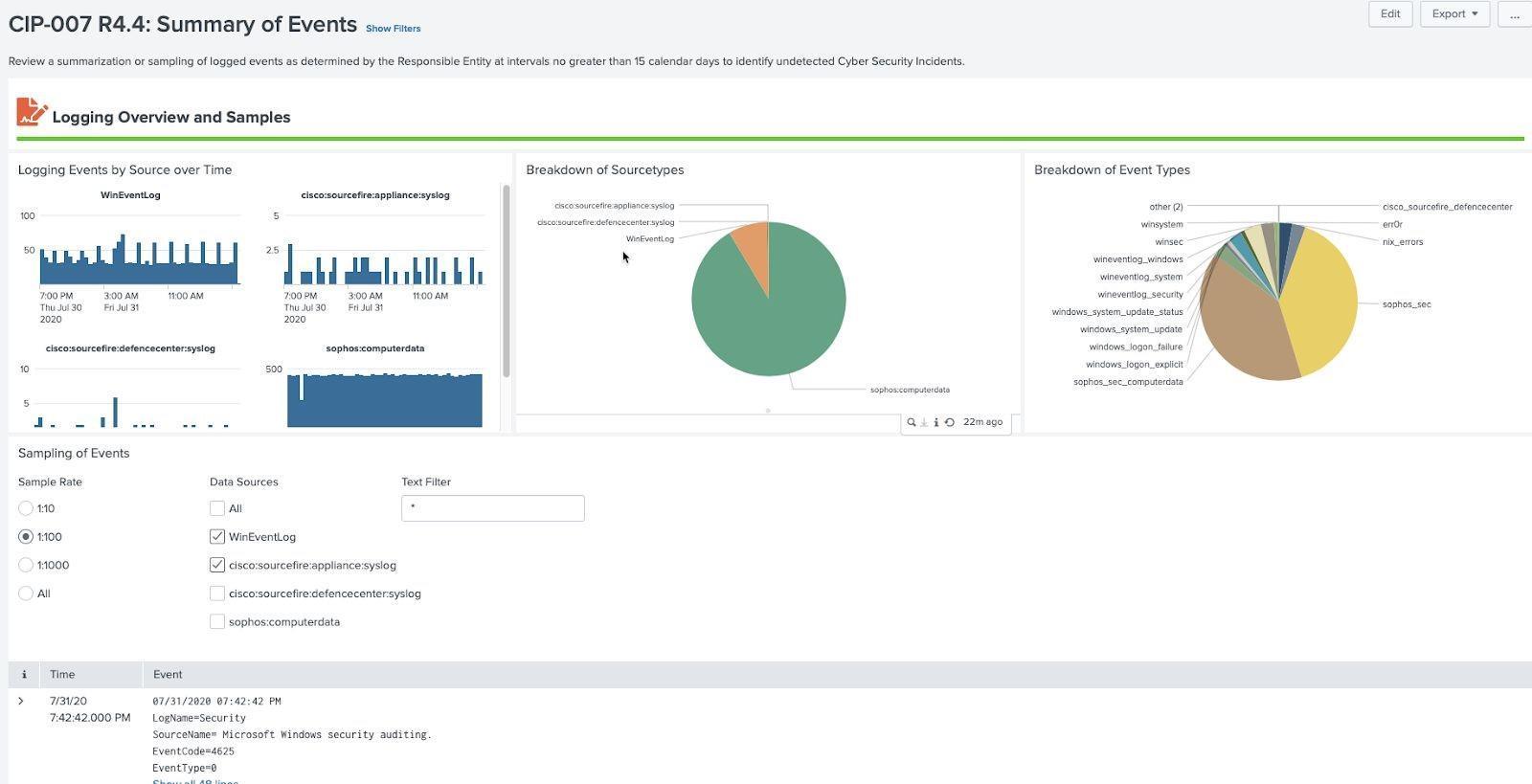
The monitoring of the NERC CIP environment is essential to understand threats to the environment. Monitoring of those alerts requires NERC environments to collect security logs and endpoint protection logs such as antivirus. In addition, NERC regulations require that logs be kept for at least 90 days and be periodically reviewed. The 5 dashboards in this section depend completely on Splunk's Common Information Models for malware, network sessions, and authentication. Since several of the requirements specify there should be a method to trigger and investigate incidents, Splunk's Enterprise Security notable and investigations features are essential to meeting several of these requirements.
Dashboards involving malware require endpoint protection to be installed, updated with signatures, and malware alerts be sent to Splunk. Those involving security logs are primarily focused on logon events, triggering security events for suspicious activity, and review of those logs.
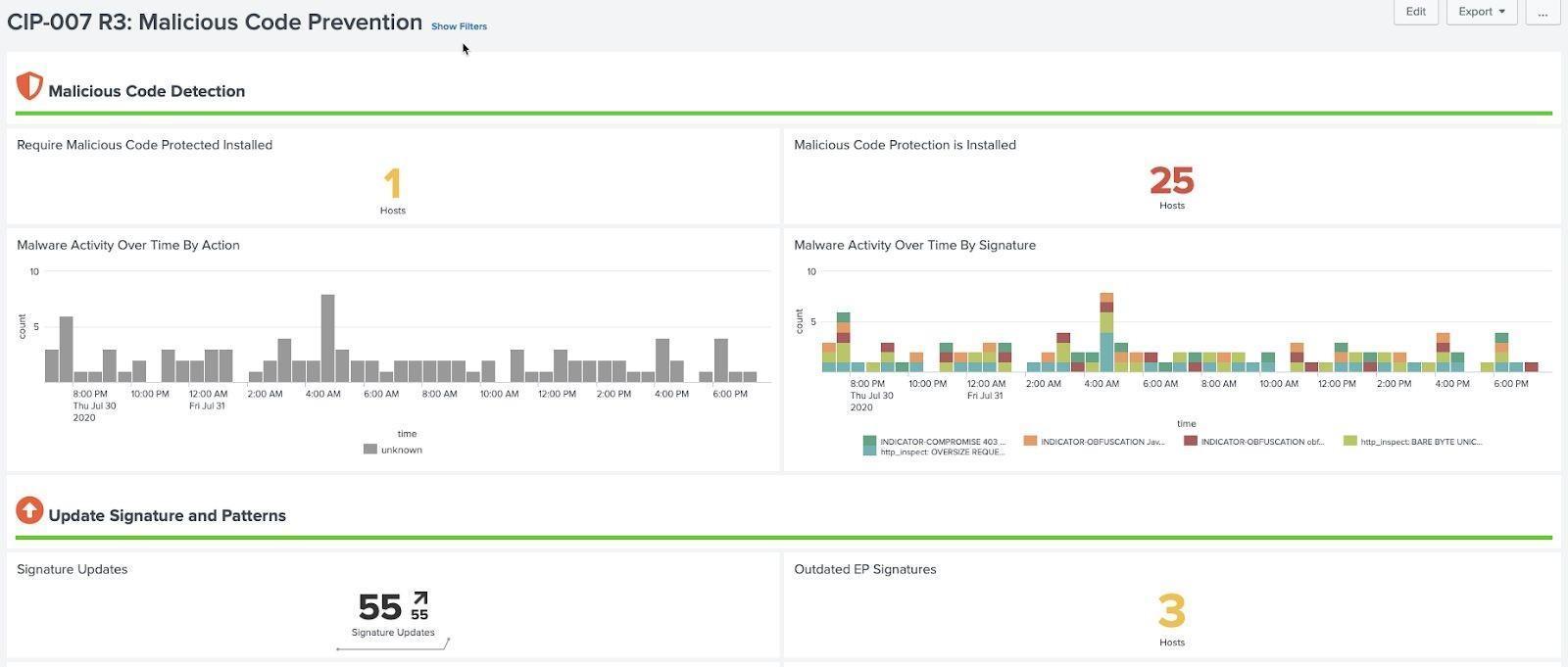
Malicious Code Prevention Example (CIP 007 R3):
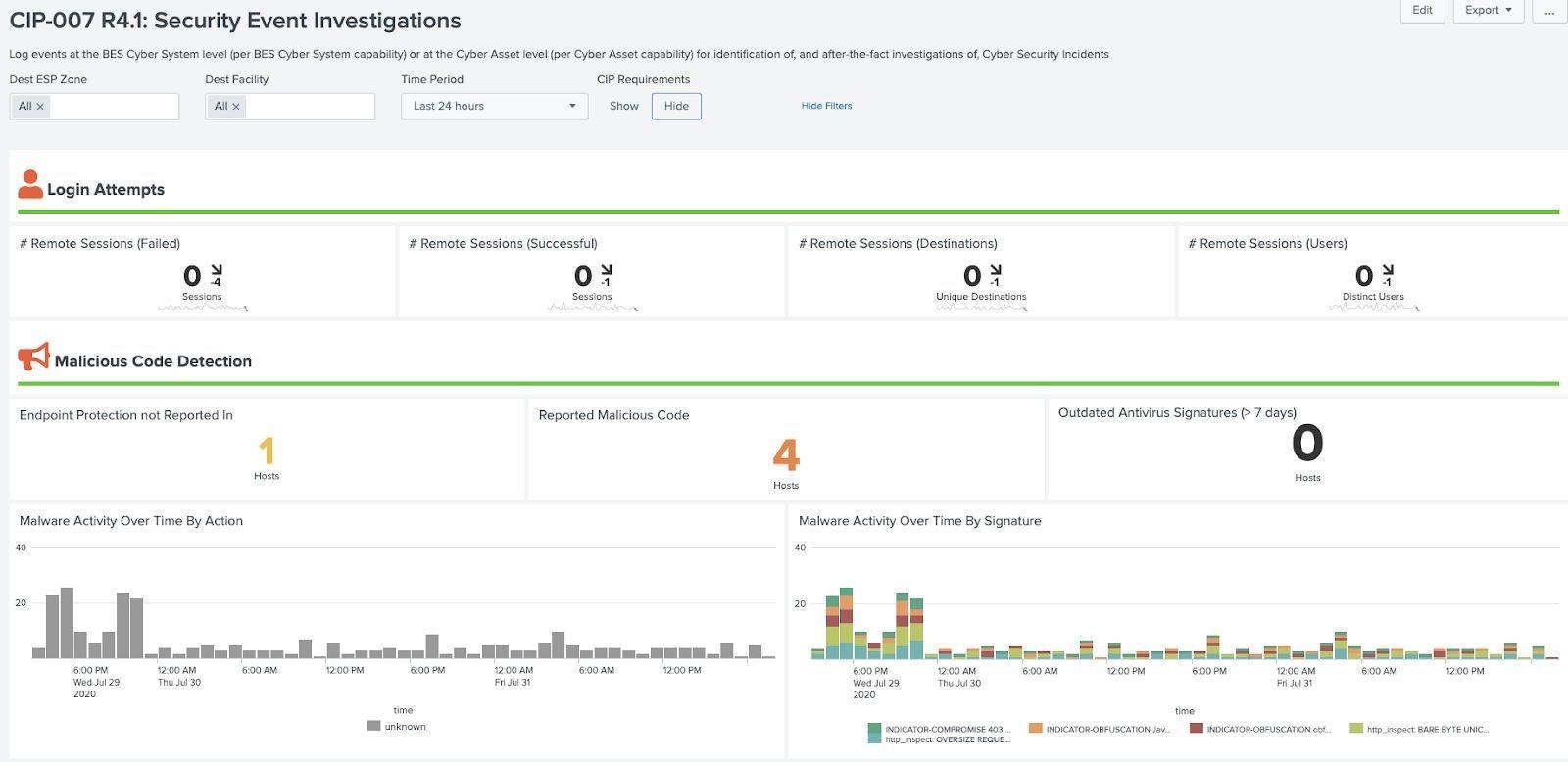
Security Event Investigations Example (CIP 004 R4.1):
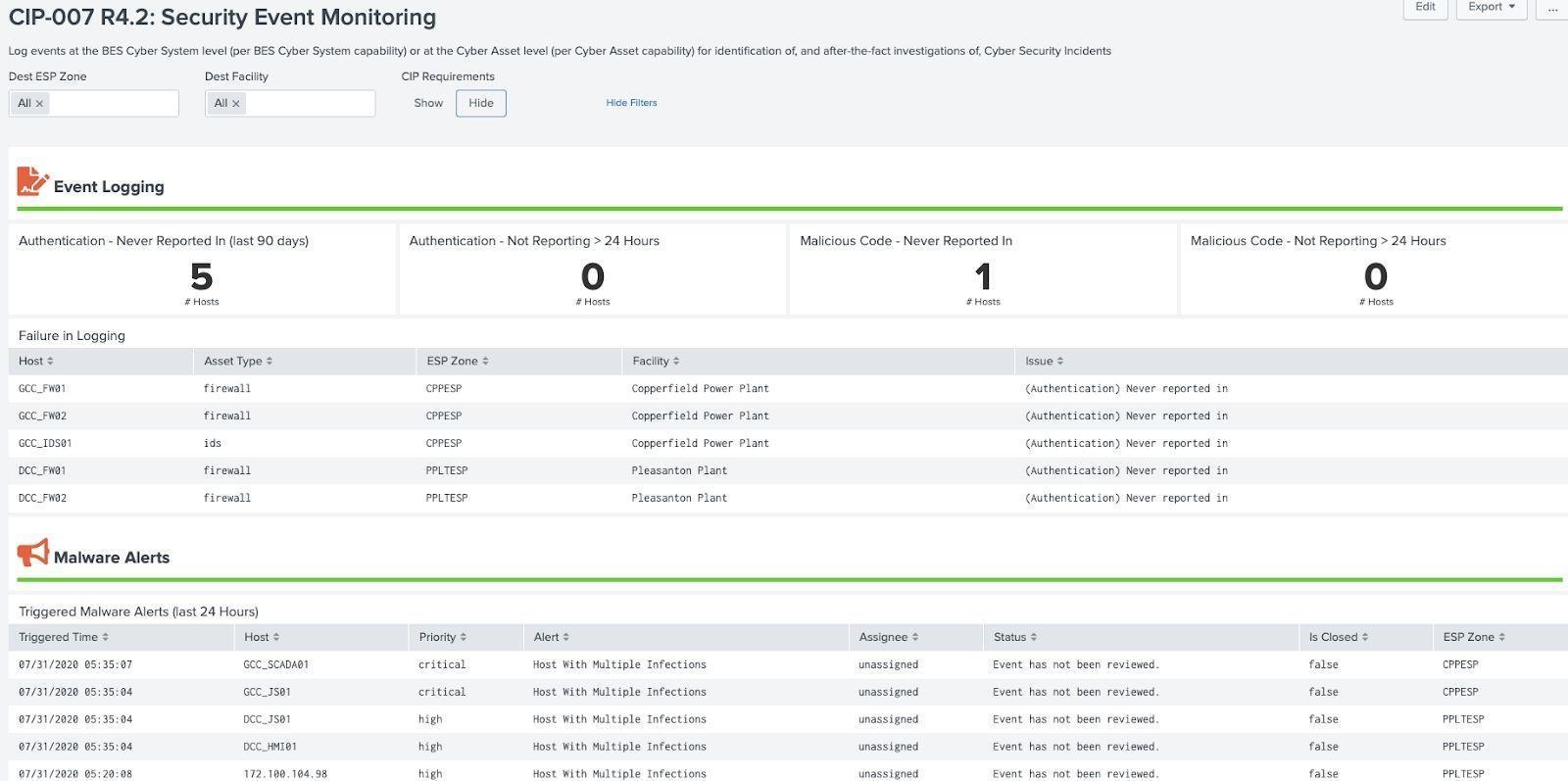
Security Event Monitoring Example (CIP 007 R4.2):
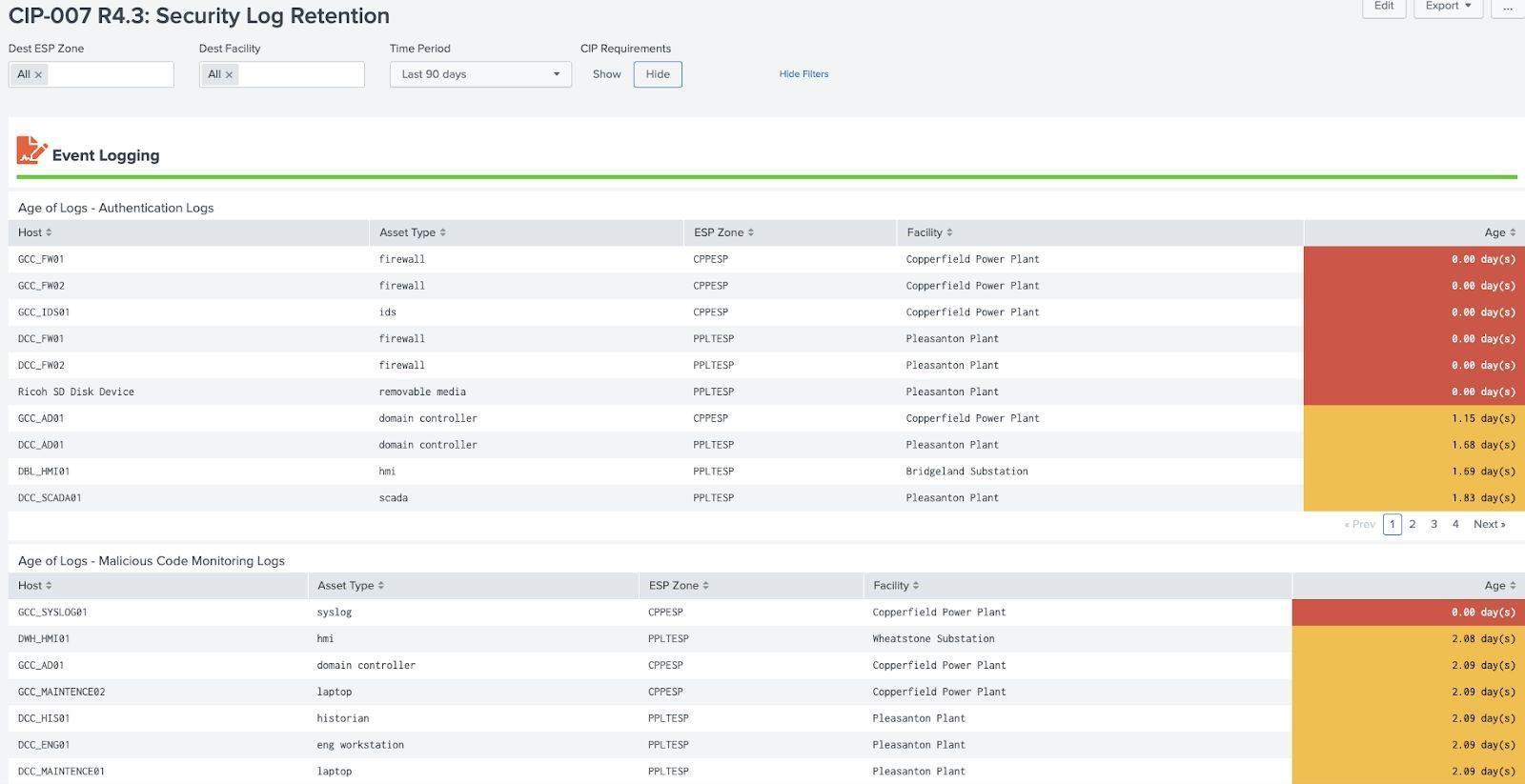
Security Log Retention Example (CIP 007 R4.3):
Summary of Events Review Example (CIP 007 R4.4):
Patching¶
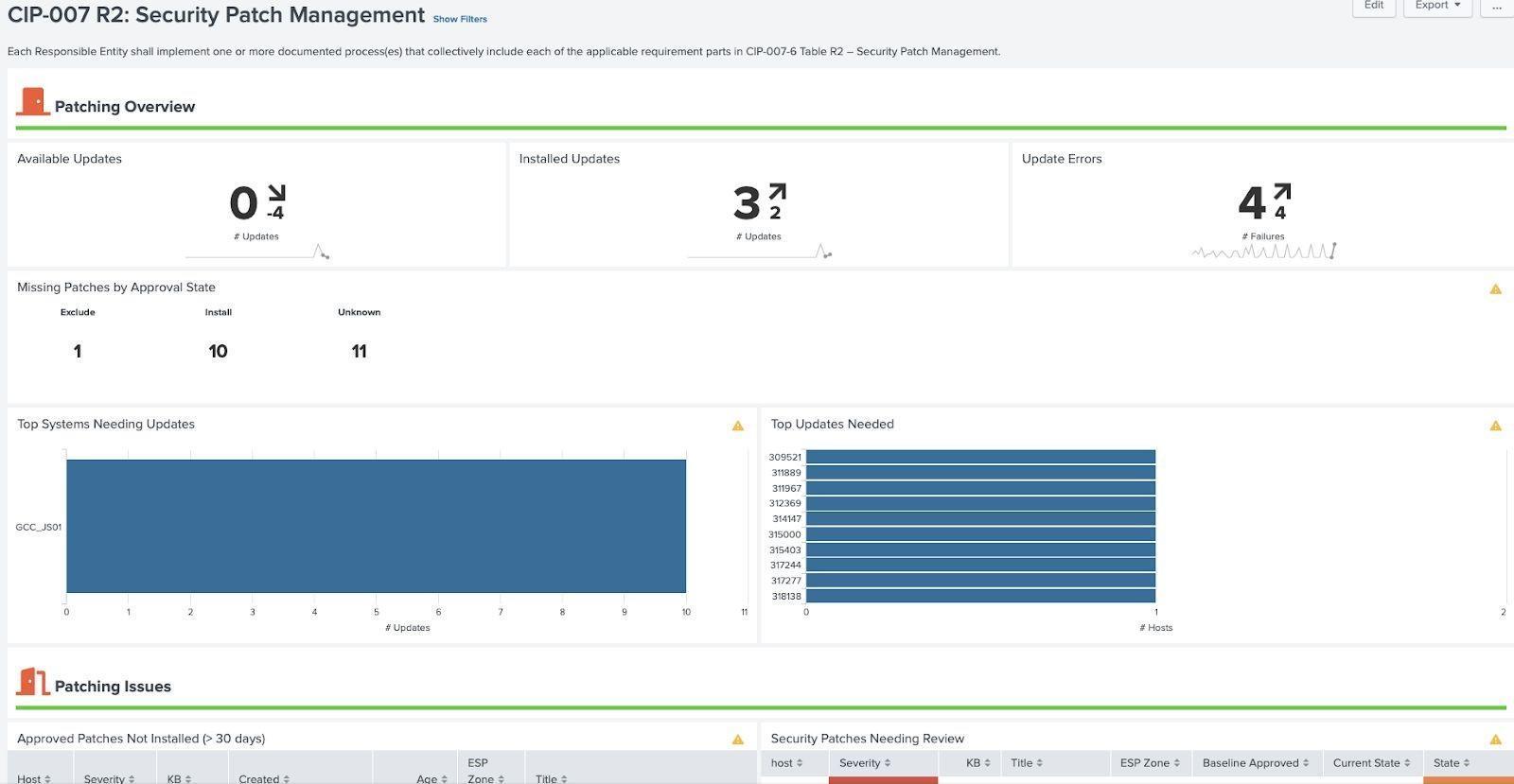
NERC CIP requires that NERC environments be updated and monitored for missing patches. In many cases, NERC environments already utilize patching solutions to help manage and approve patches (such as WSUS). In order to prevent duplication of effort, if it recommended that most of the approved patches come from existing solutions and be periodically updated. These scorecards rely on the patch baselines outlined in CIP 010 to determine when patches should be installed, as well as logs indicating patches back been installed either from the endpoint or the patching solution.
Security Patch Management Example (CIP 007 R2):
Identities¶
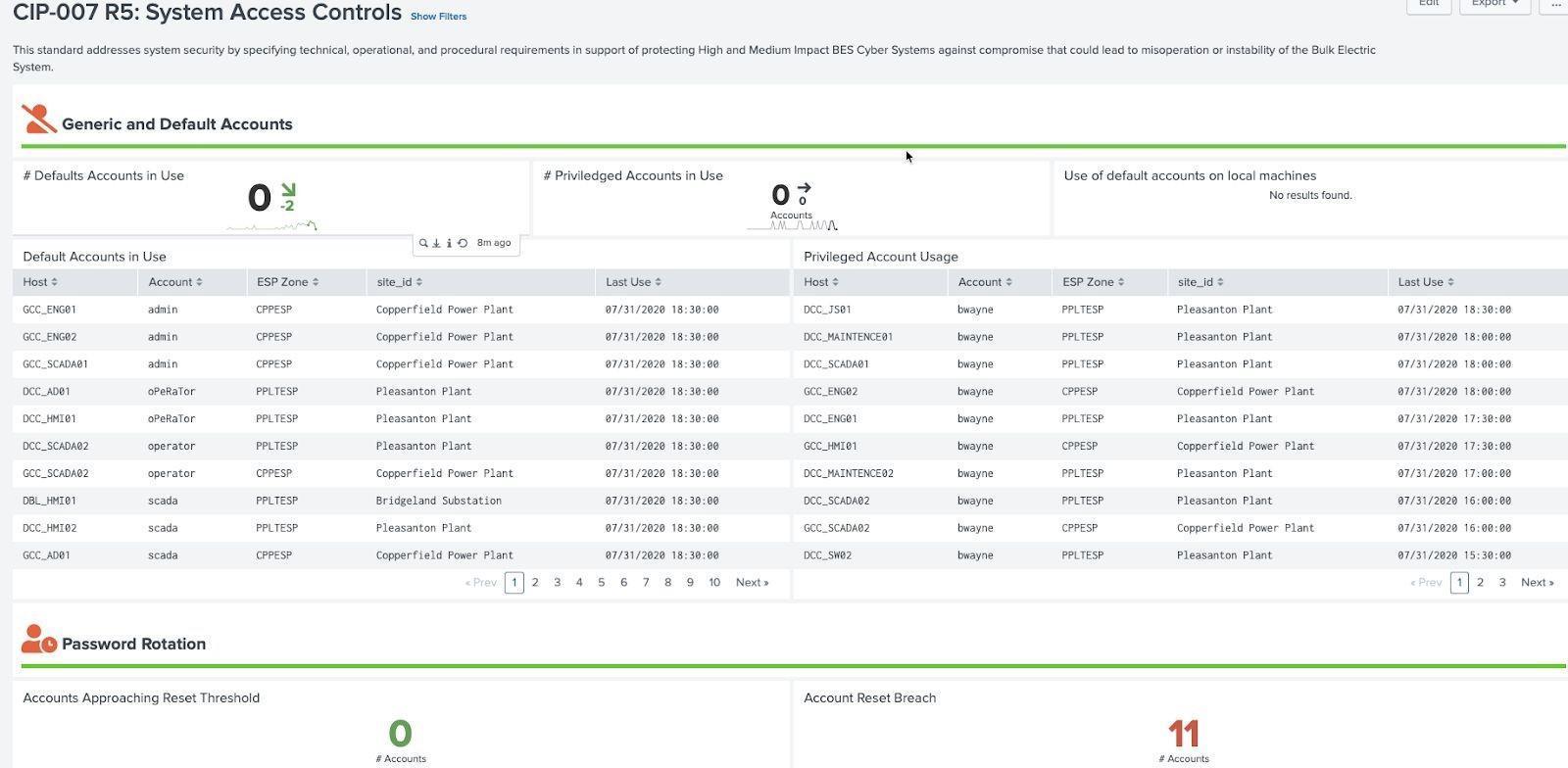
The behavior of identities and user accounts is a critical part of CIP 007, especially the use of default and privileged accounts. Since this section primarily deals with identities and heavily leverages content from the asset framework. As a result this lookup should be part of the asset framework as detailed in Section 3. Identities utilized the category field in the identities framework to designate when an account is default, generic, or privileged. This field can also be used to designate certain accounts as nerc, operations, or other classifications as needed. In addition, data regarding password changes should be included as essential for reporting purposes.
System Access Controls Example (CIP 007 R5):
NERC CIP 008¶
Cyber Security Incident Response Plan¶
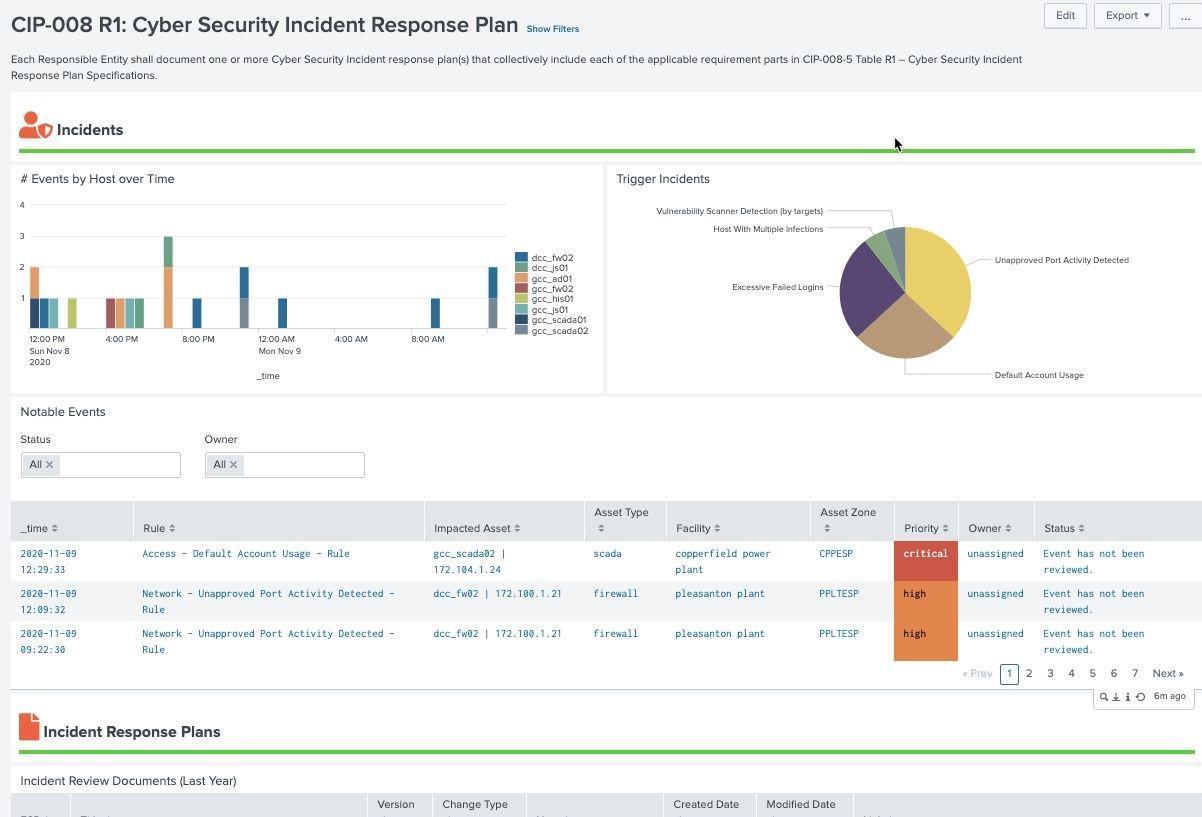
NERC CIP operators are required to have defined cyber security incident response plans (IRP) that identify how to respond to cyber incidents or violations of NERC CIP regulations. Part of this regulation requires a method to show notable or cyber incidents. This dashboard provides an overview of all the notable alerts that have been generated for NERC CIP regulated assets and is dependent on existing correlation rules built into Enterprise Security. The status and incident owner of each notable is reported to ensure incidents have been assigned and/or resolved. IRP plans should be reviewed at least yearly and updated and this dashboard provides a method to report on changes to IRP plans.
System Access Controls Example (CIP 008 R1):
NERC CIP 009¶
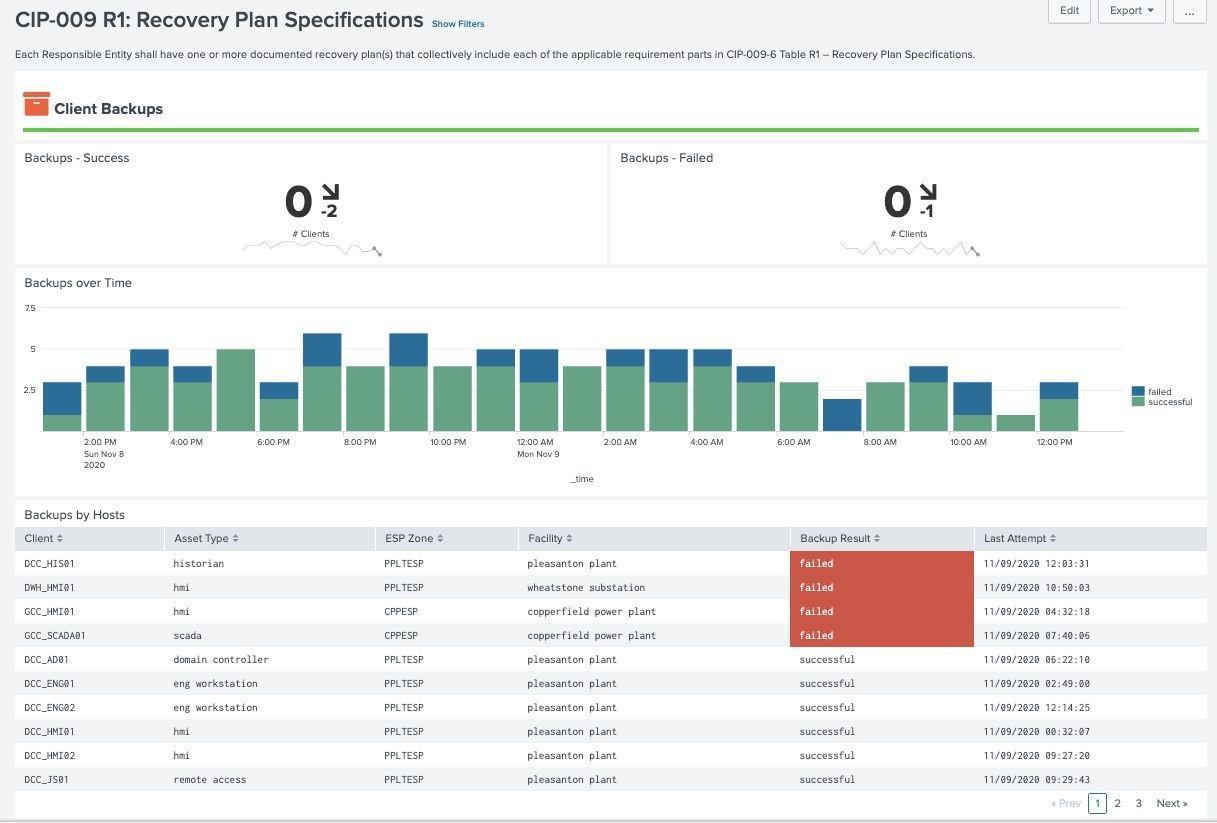
Recovery Plan Specifications¶
NERC CIP Operators are required to ensure their BES Cyber Systems can be restored quickly in case of failure or cyber attack. This includes monitoring not only the BES Cyber System but also any CIP assets which require backup. This dashboard provides information about the Splunk environment, including index retention, clustering, and Splunk features tied to High Availability and Disaster Recovery. This dashboard also brings in data from backup logs to ensure CIP assets are being backed up. The macro get_backup_indexes is used to specify data sources that contain records around client backups.
Recovery Plan Specifications Example (CIP 009 R1):
NERC CIP 010¶
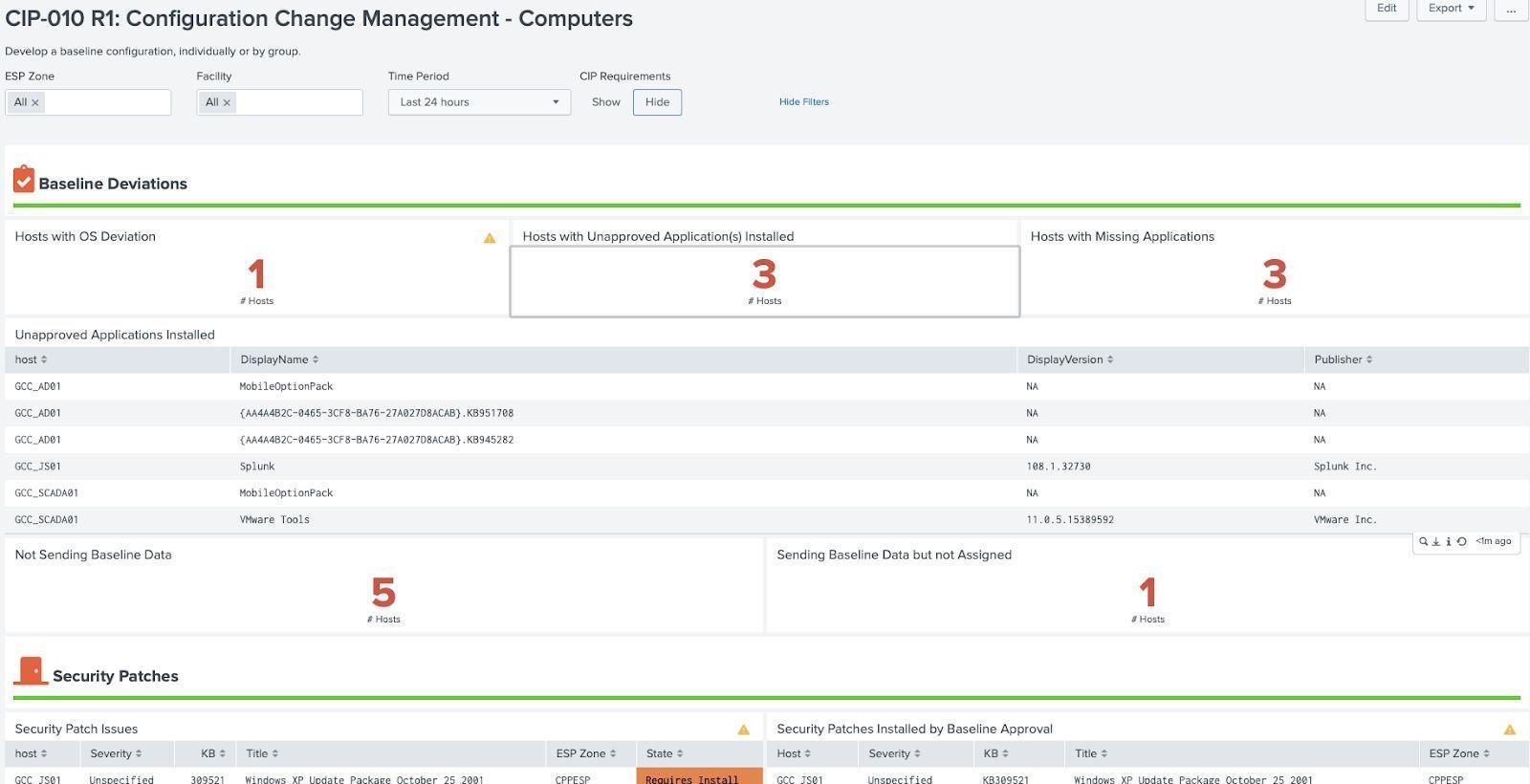
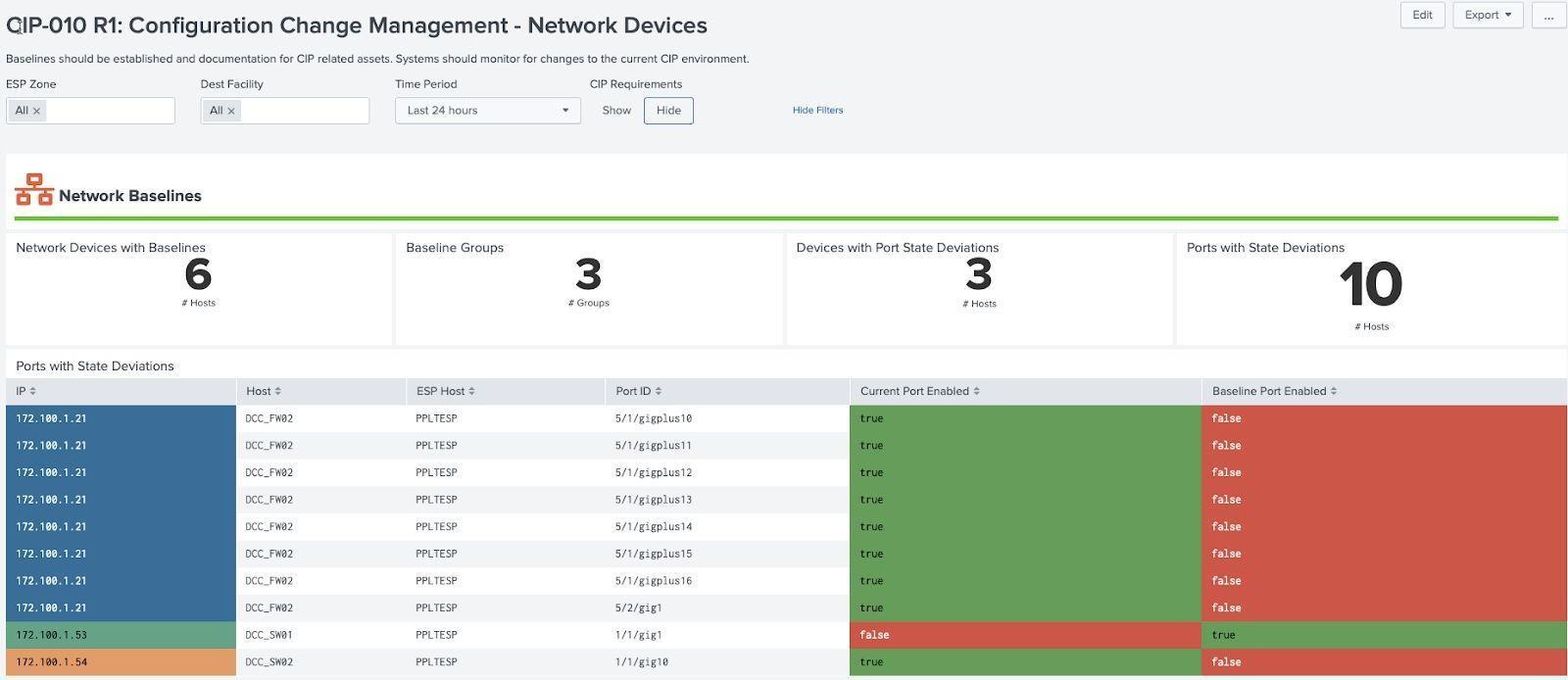
Baselining of Assets¶
Baselining of computers and network devices is required for CIP 010 compliance. Baselines can be the result of static configurations (e.g. a list of approved patches) but ideally are generated from data sources. Some good examples of data sources to consider when generating baselines are patching approval systems (such as WSUS), asset information (endpoint protection, Splunk forwarders, etc), installed software inventories, as well networking management systems. The baseline features implemented in Splunk are designed to keep track of baselines so that assets can be reviewed against specific baselines. Keeping these baselines is also required by regulation.
Assets can be grouped together so that assets within a group should match a particular configuration. Currently computer and network baselines are the only requirement kinds of baselines and each has specific elements which must be baselined. In the case of each Scorecards are designed to identify deviations from the baseline and provide information of how the item deviates from the baseline (for example, software that is installed but not approved) including hosts.
For more information of creating baselines please see Configuration Baselining Section. These dashboards are modified from the default baselining dashboards to review specifically only assets that are classified as part of NERC CIP.
Computer Baselines Example (CIP 010 R1 - Computers):
Network Baseline Example (CIP 010 R1 - Network Devices):
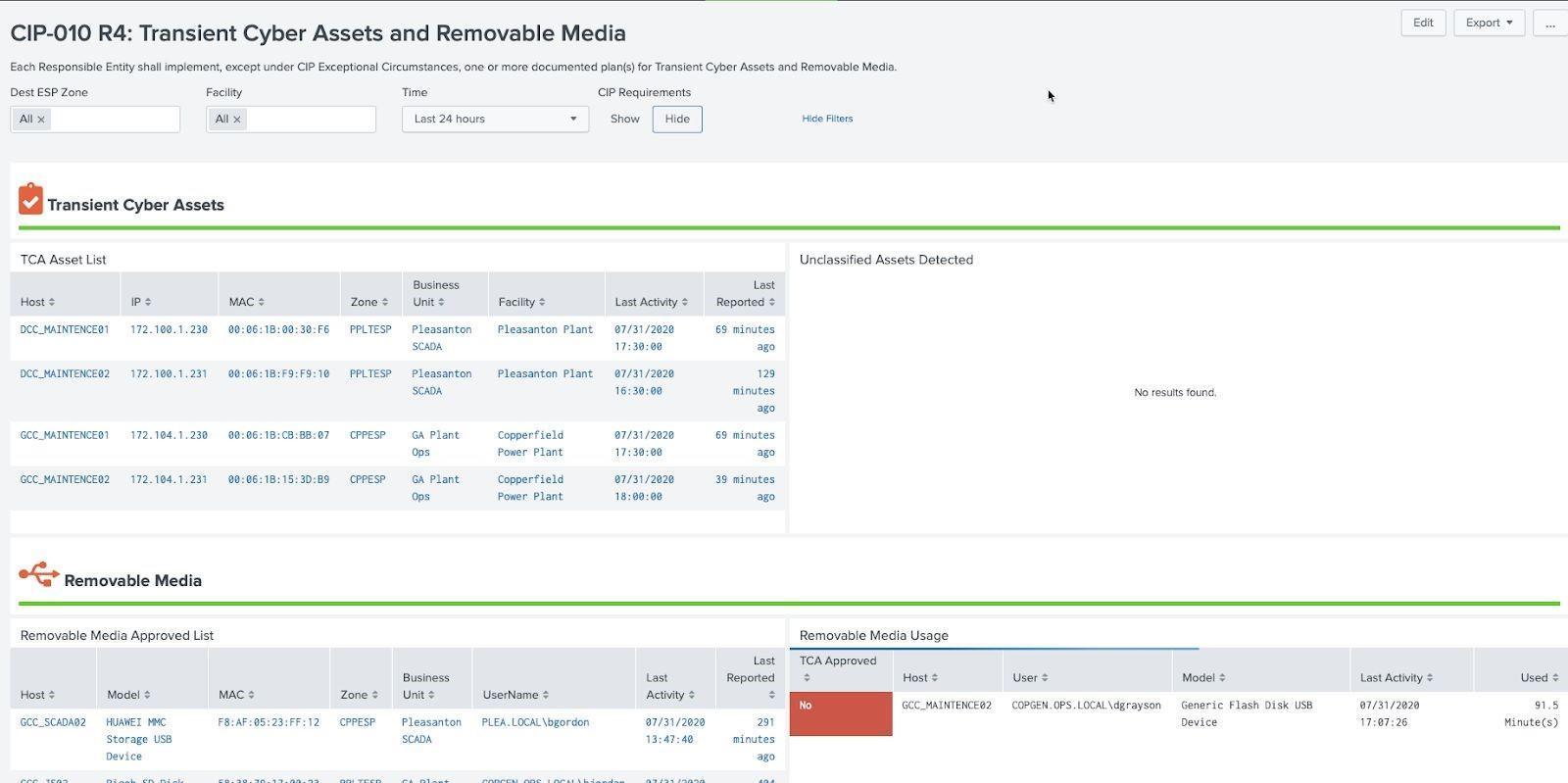
Transient Assets and Removable Media¶
Requirements exist to track transient assets such as laptops and maintenance equipment and removable media. Since transient assets are not continuously connected to networks and systems, their activity on the system should be closely tracked. The standard allows for certain removable media to be approved for general use. Assets and removable media should be classified as cip:TSA in the asset lookup for approved devices.
Transient Cyber Assets and Removable Media Example: