Integration Guidance with the OT Security Add-on for Splunk¶
Integrating with specific OT Data Models¶
Splunk for OT Security includes several data models that can be leveraged to automatically generate asset lookups. In addition, OT partners of Splunk should populate any hardware and software data captured or created by their add-ons to these data models.
Two data models have been created to facilitate populating assets into Splunk for Enterprise Security. The most critical model for asset information in the Splunk OT Security Solution is the OT Asset data model contained in the Splunk for OT Security app. This data model is designed to be used with hardware assets such as servers, PLC's, workstations, etc. and contains all fields in the OT Asset Framework. An additional data model also exists called OT Software Asset which is used to populate additional information regarding firmware, operating system, and software present on each OT asset. Together data from each can be combined to provide additional context around an asset as well as components installed on each asset.
The OT Add-on for Splunk has specific requirements for parts of the ES Asset Framework field values and formats. These fields are used to tag and identify assets as belonging to OT systems or specific classifications. More information on the data model fields can be found below. The following outline these requirements.
| Field | Restriction\Format | Sample |
|---|---|---|
ip, mac, nt_host, dns | At least one of these fields must be populated to identify an asset, multivalue values can be delimeted by using the pipe operator | 172.1.1.1 |
asset_system | Asset systems are often collections of site that may refer to a grouping of assets. While not require it is suggested for filtering purposes. | Western Operations |
category | The use of static text "ot" (without quotes) is used broadly to denote which assets are part of the OT Environment. | ot | windows | nerc |
classification | Classifications related to specific frameworks should follow the format - <framework>:<value> | cip:high | cip:BCA |
site_id | Ideally this should be populated with a name of a facility of site where the asset may reside. It is used on multiple dashboards as a filter. | Johnson Refinery |
zone | Purdue zone mappings should following the following format -- purdue:level<level #> | purdue:level3 |
Overlapping Asset Information Across Sites¶
Some vendors will re-use IP address, DNS names, and/or host names at different locations. While the site_id field can help distinguish on dashboards, the asset framework requires customization when this occurs. This specifically requires an additional field to be added to asset lookup files used by Enterprise Security called cim_entity_zone. In many cases this can be set to be the same as the site_id but can be customized as needed. For documentation on enabling this feature see the Enabling entity zones for assets and identities in Splunk Enterprise Security documentation.
Integration with Asset Inventory¶
This section outlines the basic procedures that should be used to integrate data from OT Security products with ES's Asset Framework. While each product's implementation may vary, these steps should provide additional steps to validate OT Asset information and avoid issues with bad or default values. The OT Asset Data Model should serve as the guide for field names and in the search below it is assumed mapping of field names has also been completed.
- Run the following query within the search context of the OT Security vendors add-on :
<base search>
| makemv ip delim=\"\|\"
| mvexpand ip \`\`\`split multiple ip\'s into multiple records\`\`\`
| eval ip=if(ip=\"null\", \"\", ip), nt_host=if(nt_host=\"null\", \"\", nt_host), dns=if(dns=\"null\", \"\", dns), mac=if(mac=\"null\", \"\", mac) \`\`\`remove any null string values\`\`\`
| eval ip=if(match(ip, \"\^\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\$\"), ip, \"\") \`\`\`check to verify ip is an actual ip - if you are using IPv6 you need to change this\`\`\`
| fillnull ip, dns, nt_host, mac value=\"\"
| makemv mac delim=\"\|\"
| mvexpand mac \`\`\`split multiple macs into multiple records\`\`\`
| eventstats count as mac_count by mac \`\`\`this eliminates any questionable mac\'s that may be repeated\`\`\`
| eval mac=if(mac_count \> 1, \"\", mac)
| dedup ip, dns, nt_host, mac
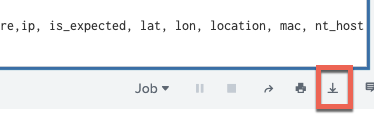
| table asset_id, asset_model, asset_status, asset_system, asset_type, asset_vendor, asset_version, asset_criticality, bunit, category, city, classification, country, dns, end_of_support, exposure,ip, is_expected, lat, lon, location, mac, nt_host, owner, parent_asset_id, pci_domain, priority, requires_av, serial, should_timesync, should_update, site_id, vlan, zone
This search takes care of several formatting issues that sometimes occur with fields like IP and ensures that they map a IPv4 format. In addition, some products may report mac's which are duplicated among assets, often belonging to a common switch, router, firewall, etc. Any duplicated mac are therefore considered suspect and removed from the asset information.
Note: The tag ot_asset is applied across all data sources. If you are focused only on a particular data set, please modify the query to specify only the selected host, sources, or sourcetypes appropriately.
-
Export the above results to a csv file using the export button
-
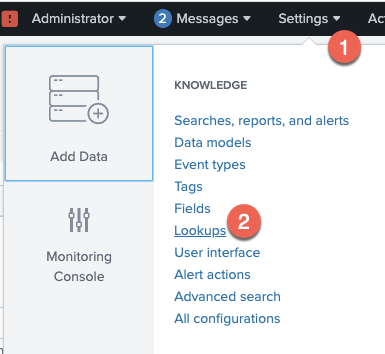
Open
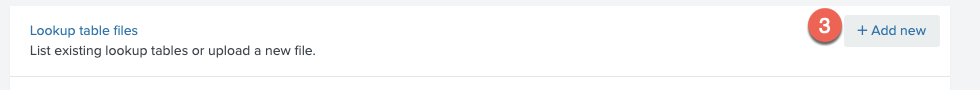
Settings → Lookups → Lookuptable files+Add New -
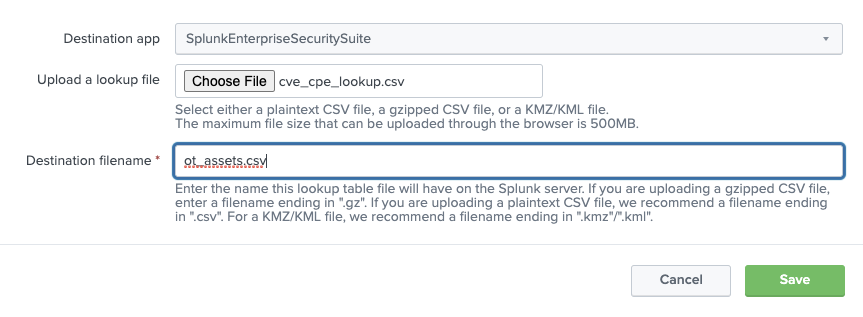
Provide the CSV file as well as an alias that will be referenced and click save
-
Change the Permissions of the lookup file in step 4 and verify is set to be shared globally
-
Open
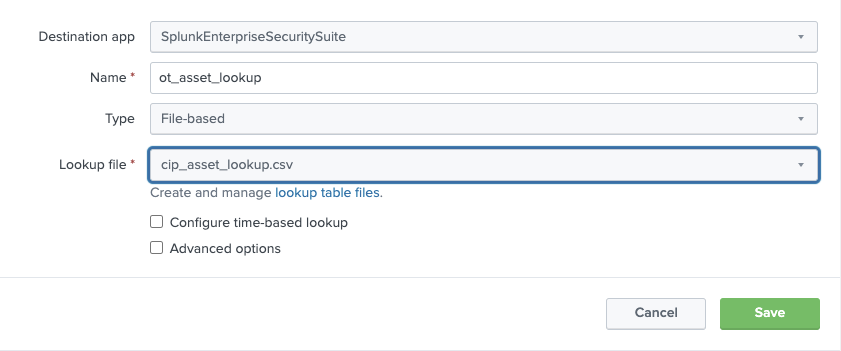
Settings → Lookups → Lookup Definitionsand click+Add New -
Create a lookup definition which references the file from step 4 and Save (note: If the file from step 4 does not show up in the lookup file dropdown list you may need to check the lookup permissions to validate it is shared globally)
-
Change the permissions on the lookup definition so it is shared globally
-
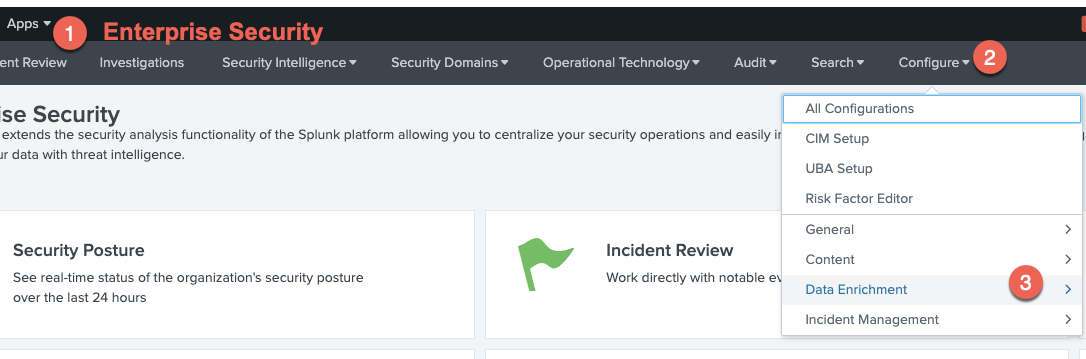
Go to the Enterprise Security App and click on the menu
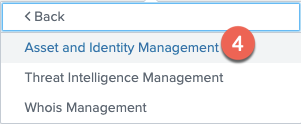
Configure → Data Enrichment → Asset and Identity Framework -
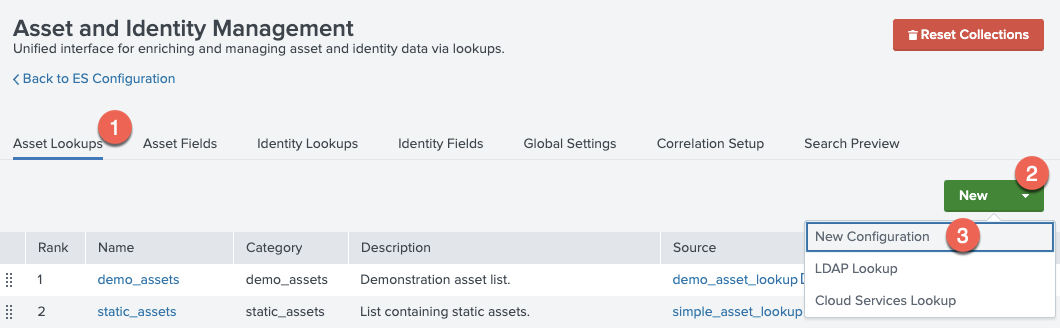
Under the Asset Lookups tab click
New → New Configuration -
Specify the following required fields:
Source,Name,Category,asset_type,site_id, andasset_system. You can leave the other field with their default values (note: if you cannot find your lookup definition you might need to validate permissions for the lookup definition is set to global) -
Validate that the file is working correctly by going to the Search Preview tab and click on
asset_lookup_by_str → Open in searchto validate assets are showing up. If your assets do not show up, look at the troubleshooting section of this document.
OT Asset Data Model¶
The following is a description of the OT Asset Data Model used in the OT Security Add-on
| Field | Sample | Description |
|---|---|---|
| asset_id | 991351 | Unique asset name or id |
| asset_model | cpu-1200 | model number of other version indicator for the asset |
| asset_status | Operational | Operational status of the asset |
| asset_system | Western Operations | Local grouping of assets, often a combination of sites or facilities into a common operational system |
| asset_type | PLC | Type of asset such as a PLC, Historian, Engineering Workstation |
| asset_vendor | Siemens | Vendor and/or Product Name |
| asset_version | 3.2 | Version of device such as a firmware version |
| asset_criticality | Critical | Operational criticality of the asset |
| bunit | commercial | Business unit that the asset belongs to |
| category | ot|nerc|distribution | Asset category, in most cases should include the tag "ot" to identify an OT device |
| city | Albuquerque, NM | Geographic location, normally including city and state |
| classification | cip:high|cip:BCA | Regulatory or other classications |
| country | USA | Geographic location, normally the country where the device resides |
| dns | scada01.ops.local | DNS name of the asset if it exists |
| end_of_support | TRUE | Boolean flag indicating whether the device is no longer supported |
| exposure | private | Measure of network exposure |
| ip | 172.1.1.1 | IP address of the asset if it exists |
| is_expected | TRUE | Flag to indicate whether the device is expected to send data to Splunk |
| lat | -45.095 | Latitiude of the asset location |
| location | line1.conveyer.plc | Logical description of where the asset resides within a site or facility |
| long | 27.2345 | Longitude of the asset location |
| mac | 00:0E:8C:41:49 | mac address of the asset |
| nt_host | scada01 | Host name of the asset |
| owner | Field Operations | Asset owner |
| parent_asset_id | 887456 | ID if the device is connected to a parent asset |
| pci_domain | POS | PCI domain that the asset belongs to |
| priority | medium | Asset priority (combined operational and security) |
| description | Safety PLC for Inbound Conveyer | Description of the asset itself |
| requires_av | TRUE | Flag indicating whether antivirus should be installed on the asset |
| serial | 10003456 | Serial number of the asset |
| should_timesync | TRUE | Flag to indicate whether an asset should be monitored for time sync events |
| should_update | FALSE | Flag to indicate whether this asset should be monitoring for patch updates |
| site_id | Borading Refinery | Facility or site name |
| vlan | 172.16.16|ot_ops | Name of the subnet or VLAN that an asset belongs to |
| zone | purdue:level3|corporate | Security zone that the asset resides in |
OT Software Asset Data Model¶
The following is a description of the OT Software Asset Data Model used in the OT Security Add-on
| Field | Sample | Description |
|---|---|---|
| asset_id | 1234567 | Unique ID assigned to software possibly from an asset management system |
| asset_name | Acrobat Reader | Name of the software, sometimes including the vendor and version information |
| category | Application | Category of the software (Firmware, OS, Application) |
| dns | scada01.ops.local | DNS name of the asset with the software installed |
| end_of_support | FALSE | Flag indicating whether the software is supported currently by the vendor |
| hash_method | SHA-2 | Function used to calculate the hash value of the software |
| hash_value | d14a028c2a3a2bc94 | Hash value of the software |
| install_date | 1686687861 | Epoch timestamp of when the software was installed |
| ip | 172.1.1.1 | IP Address of the asset with the software installed |
| licence_key | xxxxx-xxxxx-xxxx | Vendor provide asset_key for software activitation |
| mac | 00:0E:8C:41:49:C6 | Mac address of the asset with the software installed |
| nt_host | scada01 | Host name of the asset with the software installed |
| parent_asset_id | 1233445 | ID of parent asset |
| type | FTP Client | Type of software (e.g. ICS, Historian, etc) |
| vendor | Adobe | Vendor who created the software |
| version | 9.1 | Version identifier for the software |